Autonomous DEM
Configure Agent-Based Proxy for ADEM
Table of Contents
Expand All
|
Collapse All
Autonomous DEM Docs
-
AI-Powered ADEM
- AI-Powered ADEM
- Autonomous DEM for China
-
- Filter Application Experience by Time Range
- View Application Experience Across Your Organization
- View Application Experience for a Specific Application
- View Application Experience for a Specific User
- View Application Experience for Monitored Users
- View Application Experience for Branch Sites
- View Application Experience for Prisma Access Locations
- View App Acceleration Metrics with AI-Powered ADEM
- Autonomous DEM for Hybrid Workforce
- Certificate Renewal for Autonomous Digital Experience Management
- Role-Based Access Control in ADEM
- ADEM Data Collection and Agent Processes
- Manage Autonomous DEM Agent Upgrades
-
AI-Powered ADEM
- AI-Powered ADEM
- Access Experience Agent 5.1
- Access Experience Agent 5.3
Configure Agent-Based Proxy for ADEM
Learn how to configure Agent-Based Proxy support for Autonomous DEM
(ADEM).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
GlobalProtect supports sending internet traffic to an external proxy or sending internet
and private application traffic through tunnels terminating in mobile users, or a
combination of both. To support this capability, GlobalProtect runs in the following
modes:
- Proxy-only—When in proxy-only mode, GlobalProtect directs traffic exclusively to the Agent-Based Proxy without establishing a tunnel for mobile user access. Traffic for the Agent-Based Proxy follows the rules specified in the proxy auto-configuration (PAC) file.
- Tunnel-only—In tunnel-only mode, GlobalProtect operates in the same manner as previously, without redirecting traffic to the Agent-Based Proxy. It establishes a tunnel for mobile users through which all traffic is routed. All current split tunnel rules remain applicable and are supported.
- Tunnel-only Prisma Access—Tunnel-only Prisma Access mode closely resembles tunnel-only, with the exception being that in an internal network, GlobalProtect only establishes a tunnel to an external gateway. This differs from tunnel-only mode, where GlobalProtect either does not create a tunnel in an internal network or creates a tunnel to an internal gateway.
- Hybrid—In hybrid mode, GlobalProtect directs traffic to the Agent-Based Proxy according to the rules in the PAC file. Additionally, it establishes a tunnel and routes private app traffic to mobile users. All current split tunnel rules remain applicable and supported.
Customers who choose to use Agent-Based Proxy access in Prisma Access require visibility
into application access through Agent-Based Proxy as well as the performance of
Agent-Based Proxy as an element of Prisma Access' service. With ADEM, Agent-Based Proxy
forwards all internet traffic to Prisma Access and allows for customized forwarding
beyond the scope of PAC based on:
- Destination, user or user group, operating system, or location (static branch egress IPs).
- Branches with dynamic egress IP addresses.
- Geographic locations within the country.
Connect Agent-Based Proxy in ADEM
After you enable ADEM for Mobile Users, connect
Agent-Based Proxy for ADEM.
- Create a new decryption profile.
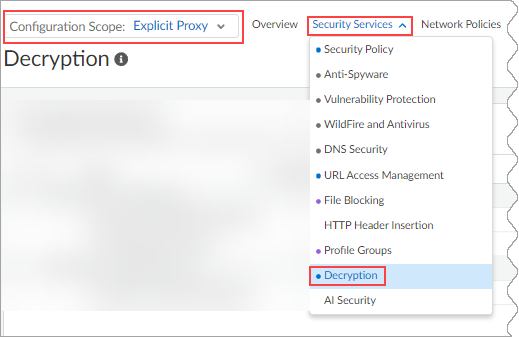
- From Strata Cloud Manager, select ManageConfigurationNGFW and Prisma Access.
- For Configuration Scope, select
Explicit Proxy, and under Security
Services, select
Decryption.

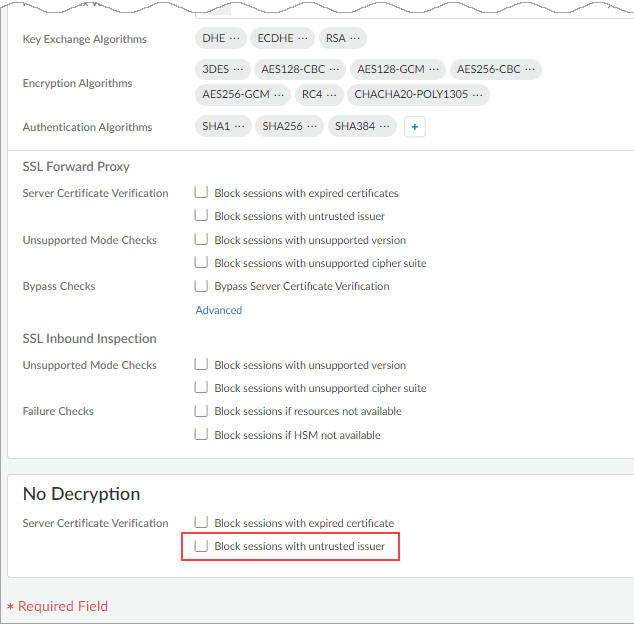
- Create a new decryption profile. Under Decryption
Profiles, select Add Profile, and
complete the required information. Ensure that the Block
sessions with untrusted issuer option under
No Decryption is not checked.

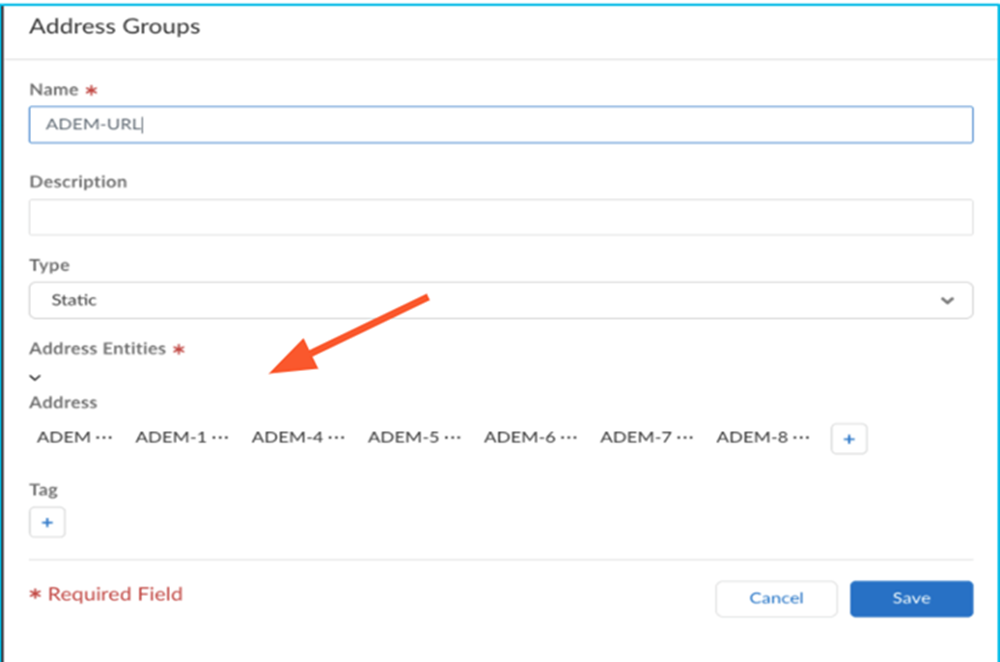
- Create an Address Group with required ADEM URLs. Navigate
to Objects, and select AddressAddress Groups. Click Add Address Group.

- Add the following ADEM URLs to the address group.
- agents.dem.prismaaccess.com
- agents.jp1.ap-northeast-1.dem.prismaaccess.com
- agents.sg1.ap-southeast-1.dem.prismaaccess.com
- agents.au1.ap-southeast-2.dem.prismaaccess.com
- agents.ca1.ca-central-1.dem.prismaaccess.com
- agents.eu1.eu-central-1.dem.prismaaccess.com
- agents.uk1.eu-west-2.dem.prismaaccess.com
- agents.us1.us-east-2.dem.prismaaccess.com
- updates.dem.prismaaccess.com
- agents.in1.ap-south-1.dem.prismaaccess.com
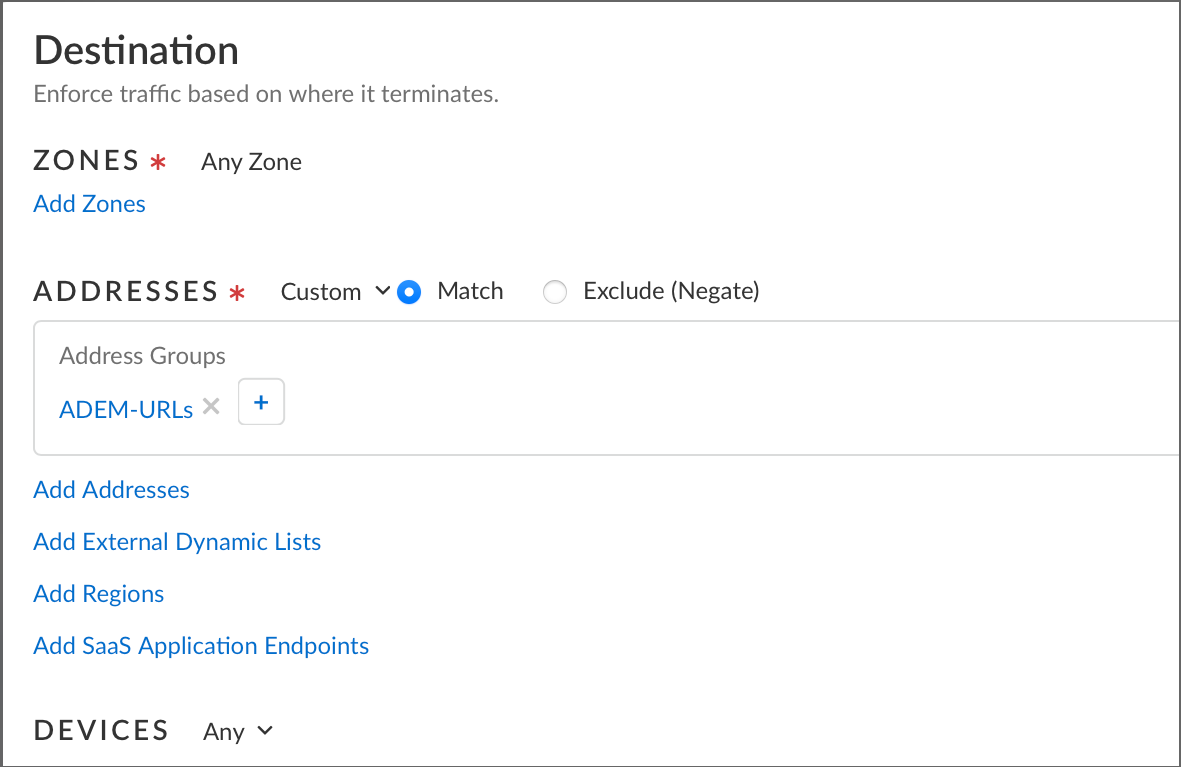
- Create a Security policy rule and add the newly created address group object to it.To do so, click the + icon under DestinationAddresses and add the address group you created, as shown in the following image.

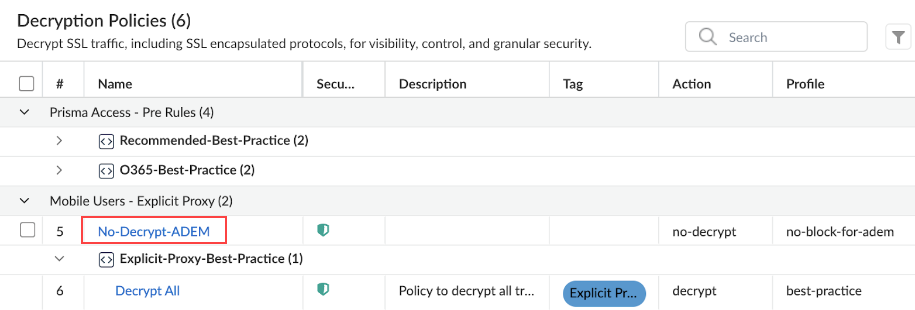
- Create a new decryption policy. Navigate back to Security ServicesDecryption, and in Decryption Policies , click
Add Rule.
- Name the decryption policy; for example, No-Decrypt-ADEM.
- Under Destination, select Address Groups, and add the Address Group you created in step 2.
- Under Action and Advanced Inspection:
- Under Action, select Do Not Decrypt.
- Under Decryption Profile, select the Decryption Profile you created in step 1.
- Under Decryption Policies, move the new
No-Decrypt-ADEM policy above the default
Decrypt All policy so the newly created policy is
preferred for ADEM destinations. For non-ADEM destinations, the
Decrypt All policy is present, so moving the new
policy does not alter any existing security posture.