Enterprise DLP
Create an Endpoint DLP Policy Rule
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Create an Endpoint DLP Policy Rule
Create an Endpoint DLP policy rule to prevent exfiltration of sensitive data over
peripheral devices.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
| Prisma Access (Managed by Strata Cloud Manager) |
|
Enterprise Data Loss Prevention (E-DLP) supports creation of the following types of Endpoint DLP
policy rules.
- Peripheral Control—Policy rule to granularly control who in your organization can use peripheral devices. You can block access to multiple user groups while excluding others.
- Data in Motion—Policy rule to inspect and block exfiltration of sensitive data moving between an endpoint and a peripheral device. Traffic that matches your Endpoint DLP policy rule is forwarded to Enterprise DLP inspection and verdict rendering.
Endpoint DLP policy rules are evaluated in a top-down priority. This means that in
the event that two policy rules in the rule hierarchy apply to the same users and
peripherals, Enterprise DLP takes the Response action
based on the first policy rule that was matched.
After pushing your Endpoint DLP policy rule, you can view your audit and push logs to
review your configuration change history and to verify the configuration change was
successfully pushed to the Prisma Access Agent.
Palo Alto Networks recommends reviewing the Endpoint DLP policy rule example before
you create your Peripheral Control and Data in Motion policy rules. In this example,
example, we create two Endpoint DLP policy rules. The first is a Policy Control
policy rule to block access to USB peripheral devices for all users while excluding
a specific user group for which you allow access to USB peripherals. The second is a
Data in Motion policy rule to prevent exfiltration of sensitive data from the
endpoint to the peripheral for those users associated with the excluded user group
using Enterprise DLP.
Data in Motion Policy Rules for Printer peripherals
Enterprise DLP inspects only the first five pages of a document and the
first five images included in an inspected file when traffic matches a data in
motion policy rules for Printer peripherals.
The total number of data patterns across all your Endpoint DLP policy rules, the
size of the inspected file, and the total number of images within the file all
impact the time it takes for Enterprise DLP to inspect the file. This is
referred to as the Max Latency. Enterprise DLP
is unable to render a verdict if the inspection time exceeds the max
latency.
To control the default action Enterprise DLP takes when the max latency is
reached, edit the Action When Max Latency is Reached in
the Endpoint DLP Data Transfer settings.
Endpoint DLP Policy Rule Example
Example of creating Endpoint DLP policy rules to control access to peripheral devices
for some users while allowing access to other users.
- Log in to Strata Cloud Manager.Add a Peripheral to Endpoint DLP and Create a Peripheral Group.Adding peripheral devices and creating peripheral groups is required only if you want to allow or block access to specific peripheral devices. You can skip this step if you want to allow or block access to all peripheral devices of any type.Repeat this step to add all peripheral devices you want to control access to using Endpoint DLP. In this example, we are allowing access to a specific peripheral group.Configure the Enterprise DLP match criteria to define custom sensitive data that you want to inspect for and block in your Data in Motion policy rule.
- Create custom data patterns to define your match criteria.Alternatively, you can use the predefined data patterns instead of creating custom data patterns.Create a data profile and add your data patterns.Alternatively, you can use the predefined data profiles instead of creating custom data profiles.Select ConfigurationData Loss PreventionEndpoint DLP Policy and Add Policy.Create a Peripheral Control policy rule.In this example, we want to configure a policy rule that restricts endpoint access to all USB peripheral devices for all users, while excluding two users approved to have USB connectivity for their endpoints.
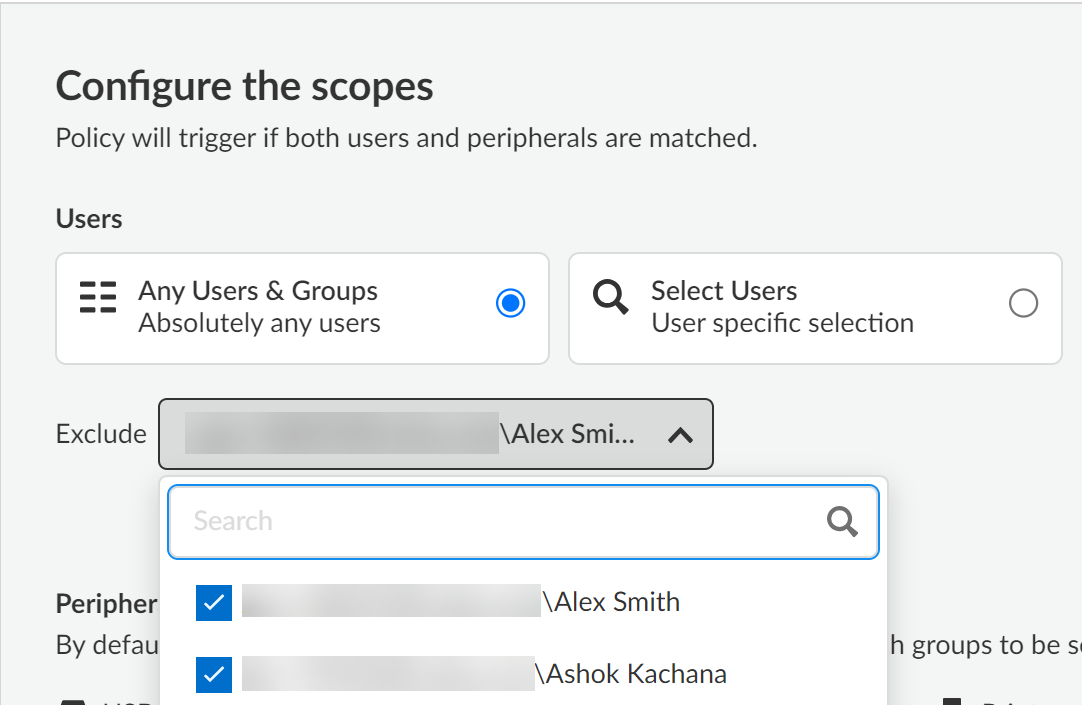
- Configure the Basic Information for the Peripheral Control policy rule.Make sure that you Enable Policy. Click Next to continue.For the Scope, select Any Users & Groups.This option blocks access to all users regardless of the user group they are associated with. You can exclude one or more users, thereby allowing their endpoint connectivity to USB peripheral devices you specify.In the example below, the Peripheral Control policy rule Scope is configured to block access to all users while allowing endpoint connectivity to USB peripheral devices for Alex Smith and Ashok Kachana.
![]() For the Peripherals, select Any to block connectivity to all USB peripheral devices. Alternatively, you can Select specific USB peripheral devices to Include or Exclude.
For the Peripherals, select Any to block connectivity to all USB peripheral devices. Alternatively, you can Select specific USB peripheral devices to Include or Exclude.- If you Include specific USB peripheral devices then endpoint connectivity to only the specified USB peripheral devices is blocked. All other USB peripheral device connectivity is allowed.
- If you Exclude specific USB peripheral devices then endpoint connectivity is blocked for all but excluded USB peripheral devices.
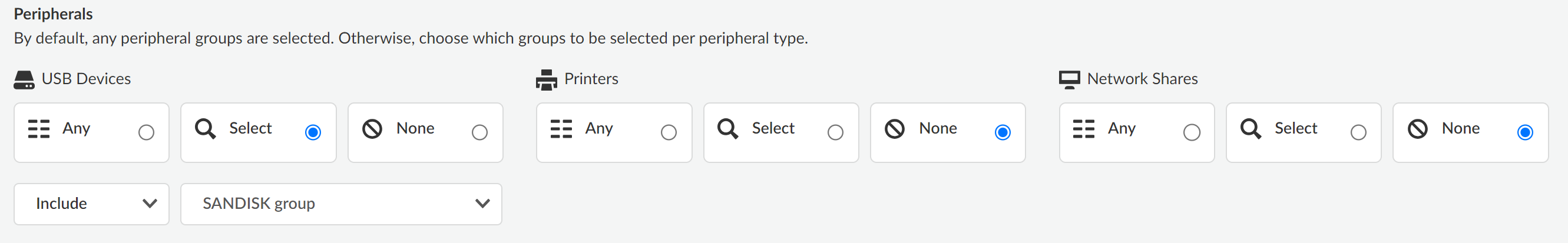
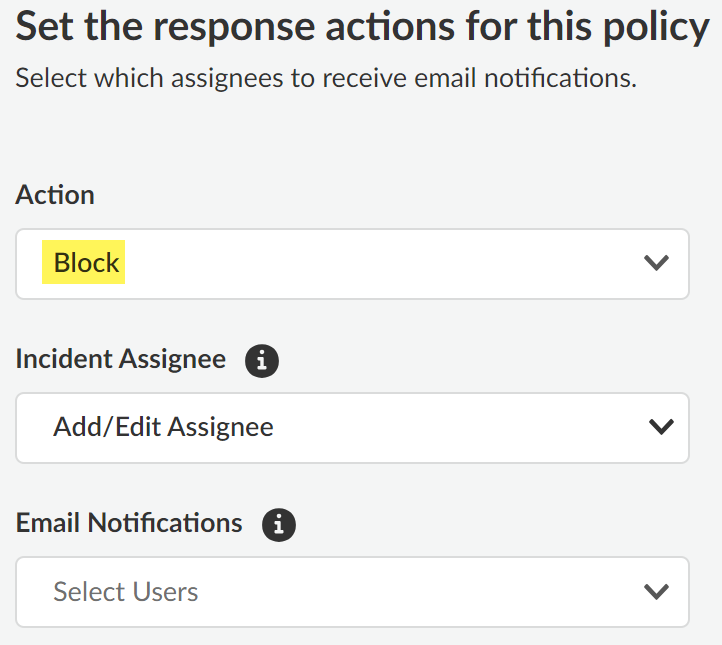
In this example, Any is selected because we want to block endpoint connectivity for all USB peripheral devices. This particular policy rule is specific to USB devices so None is selected for Printers and Network Shares.![]() Click Next to continue.For the Response Action, select Block.
Click Next to continue.For the Response Action, select Block.![]() Click Next to continue.For the Evaluation Priority, configure the Priority Selection as 1st.Palo Alto Networks recommends adding Peripheral Control policy rules designed to block access to peripheral devices at the top of your policy rulebase hierarchy. This ensures that the correct users are blocked and not unintentionally given access.Click Next to continue.Review the Endpoint DLP policy rule Summary and Save.Create a Data in Motion policy rule.In this example, we want to configure a policy rule that restricts uses Enterprise DLP to prevent exfiltration of sensitive data for the users we excluded in the Peripheral Control policy rule.
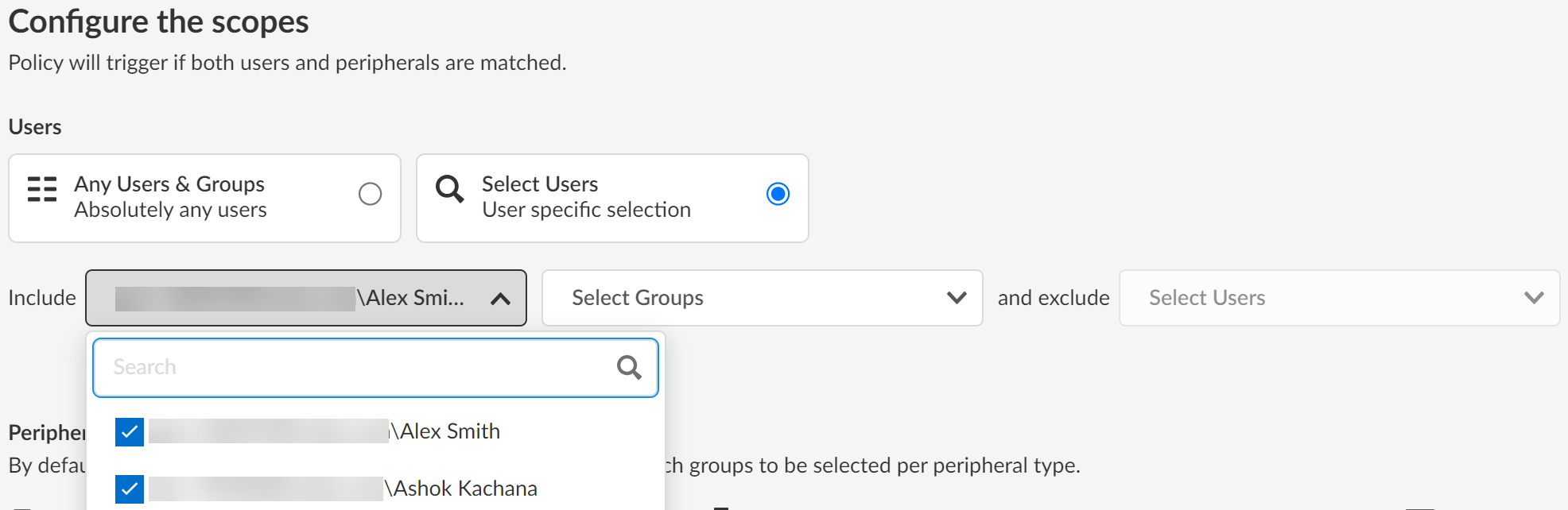
Click Next to continue.For the Evaluation Priority, configure the Priority Selection as 1st.Palo Alto Networks recommends adding Peripheral Control policy rules designed to block access to peripheral devices at the top of your policy rulebase hierarchy. This ensures that the correct users are blocked and not unintentionally given access.Click Next to continue.Review the Endpoint DLP policy rule Summary and Save.Create a Data in Motion policy rule.In this example, we want to configure a policy rule that restricts uses Enterprise DLP to prevent exfiltration of sensitive data for the users we excluded in the Peripheral Control policy rule.- Configure the Basic Information for the Data in Motion policy rule.Make sure that you Enable Policy. Click Next to continue.For the Classifiers, select the Data Profile you created in the previous step or select a predefined data profile.Click Next to continue.For the Scope, select Select Users.This option allows you to select the specific users for to which the policy rule applies while excluding all other users.In the example below, the Data in Motion policy rule Scope is configured to inspect file movement from the endpoint devices of Alex Smith and Ashok Kachana to the USB peripheral devices you specify in the next step.
![]() Click Next to continue.For the Peripherals, Select a USB peripheral groups to Include or Exclude.
Click Next to continue.For the Peripherals, Select a USB peripheral groups to Include or Exclude.- If you Include specific USB peripheral group then Enterprise DLP inspects and renders verdicts on file movement between the endpoint device and all the specified USB peripheral devices associated with the selected peripheral groups. Enterprise DLP inspection and verdict rendering doesn't occur for file movement for any other USB device.
- If you Exclude one or more USB peripheral groups then Enterprise DLP inspects and renders verdicts on file movement between the endpoint device and all but the excluded USB peripheral groups.
In this example, we included the SANDISK group to allow write access to a specific set of USB devices and we want Enterprise DLP inspection and verdict rendering for these USB peripheral devices when connected to Alex and Ashok's endpoints. This particular policy rule is specific to USB devices so None is selected for Printers and Network Shares.![]() Click Next to continue.For the Response Action, select Block.This instructs Enterprise DLP to block file movement from the endpoint to the USB peripheral device if sensitive data is detected.
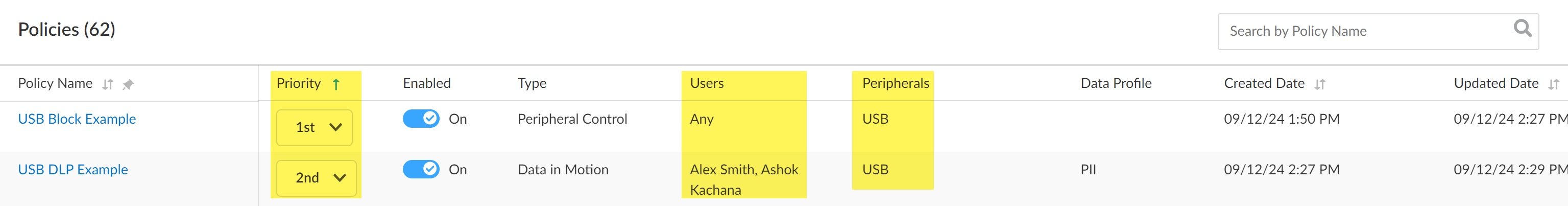
Click Next to continue.For the Response Action, select Block.This instructs Enterprise DLP to block file movement from the endpoint to the USB peripheral device if sensitive data is detected.![]() Click Next to continue.For the Evaluation Priority, configure the Priority Selection as 2nd.Palo Alto Networks recommends adding the Data in Motion policy rules after your Peripheral Control policy rules to ensure the correct users are blocked and not unintentionally given access while forwarding traffic for allowed users to Enterprise DLP.Click Next to continue.Review the Endpoint DLP policy rule Summary and Save.Review your Endpoint DLP policy rulebase to verify your policy rules are enabled and ordered correctly.Review the Priority to ensure your policy rules are ordered correctly, the Users to confirm your policy rules target the correct set of users, and the Peripherals to ensure the policy rules apply to the intended peripheral device types.
Click Next to continue.For the Evaluation Priority, configure the Priority Selection as 2nd.Palo Alto Networks recommends adding the Data in Motion policy rules after your Peripheral Control policy rules to ensure the correct users are blocked and not unintentionally given access while forwarding traffic for allowed users to Enterprise DLP.Click Next to continue.Review the Endpoint DLP policy rule Summary and Save.Review your Endpoint DLP policy rulebase to verify your policy rules are enabled and ordered correctly.Review the Priority to ensure your policy rules are ordered correctly, the Users to confirm your policy rules target the correct set of users, and the Peripherals to ensure the policy rules apply to the intended peripheral device types.![]() Review your Endpoint DLP Audit and Push Logs.Review your Enterprise DLP Incidents.A DLP incident is generated when a user moves a file from the endpoint to the peripheral device but sensitive data is detected and the file move is blocked because sensitive data was detected.
Review your Endpoint DLP Audit and Push Logs.Review your Enterprise DLP Incidents.A DLP incident is generated when a user moves a file from the endpoint to the peripheral device but sensitive data is detected and the file move is blocked because sensitive data was detected.Create an Endpoint DLP Peripheral Control Policy Rule
Create a peripheral control Endpoint DLP policy rule to granularly control who in your organization can use peripheral devices.- Log in to Strata Cloud Manager.Select ConfigurationData Loss PreventionEndpoint DLP Policy and Add Policy.Configure the Basic Information.
- For the Policy Type, select Peripheral Control.Enter a descriptive Name for the Endpoint DLP policy rule.(Optional) Enter a Description to describe the Endpoint DLP policy rule.Select the Severity of the Enterprise DLP incident when sensitive data is moved between an endpoint and a peripheral device.Enable Policy is enabled by default and enables the Endpoint DLP policy rule after you save.Disable this setting if you don't want to immediately enable the Endpoint DLP policy rule after creation.Click Next to continue.Configure the Scope to define which users can use peripheral devices.For Enterprise DLP to take the configured Response action, both Users and Peripherals must be matched.
- Select the Users the policy rule applies to.
- Any Users & GroupsCreate a peripheral control policy rule that applies to all users. Additionally, you can Exclude one or more users from the peripheral control policy rule.
- Select Users & GroupsCreate a peripheral control policy rule that applies to specific users and groups. You can configure the policy rule to apply to either specific users or user groups, or to both.Include
- Select Users—Select one or more specific users to which the rule applies.
- Select Groups—Select one or more user groups to which the rule applies.
Exclude—Select one or more users to exclude from the peripheral control policy group. You must select at least one user group in order to exclude one or more users.
Select the Peripherals you want to allow or block access to.You can define user access to USB devices, printers, and network shares in a single peripheral control policy rule. The access configuration for each type of peripheral device are independent of each other and can be configured as needed. For example, you can create a policy rule to block access to all USB devices, allow access to all printers, and allow access to only specific network shares you selected.- Any (default)—Policy rule applies all USB, printer, or network share peripherals peripherals added to Enterprise DLP.
- Select— Policy Rule applies only to the selected peripheral devices or peripheral groups.
- None—Policy rule doesn't apply to any USB, printer, or network share peripherals added to Enterprise DLP.
Click Next to continue.Configure the Response to define the action Enterprise DLP takes when a user access a blocked peripheral.- Action—Action Enterprise DLP takes if a User accesses a Peripheral device defined in the policy rule Scope.
- Block—Enterprise DLP generates a DLP incident and blocks the endpoint from accessing the peripheral.
- Incident Assignee—The administrator the Enterprise DLP incident is assigned to if one is generated against the policy rule.
- Email Notifications—Add administrators to send email notifications when an incident is generated against the policy rule.
Click Next to continue.Define the Evaluation Priority for the peripheral control policy rule in your Endpoint DLP policy rulebase.You can use the Priority Selection to quickly insert the peripheral control policy rule in the appropriate location in your policy rulebase hierarchy.click Next to continue.Review the policy rule Summary to verify its configured correctly and Save.Push your Endpoint Policy rule.- Select Push Policies and Push Policies.(Optional) Enter a Description for the Endpoint DLP policy push.Review the Push Policies scope to understand which Endpoint DLP policy rules and peripheral group configuration changes are included in the push.Push.Review your Endpoint DLP Audit and Push Logs.Review your Enterprise DLP Incidents.A DLP incident is generated when a user moves a file from the endpoint device to the peripheral but you have blocked all access to a peripheral device type.
Create an Endpoint DLP Data in Motion Policy Rule
Create a data in motion Endpoint DLP policy rule to inspect and block sensitive data between moving between an endpoint and a peripheral device.- Log in to Strata Cloud Manager.Configure the Enterprise DLP match criteria to define custom sensitive data that you want to inspect for and block.
- Create custom data patterns to define your match criteria.Alternatively, you can use the predefined data patterns instead of creating custom data patterns.Create a data profile and add your data patterns.Alternatively, you can use the predefined data profiles instead of creating custom data profiles.Select ConfigurationData Loss PreventionEndpoint DLP Policy and Add Policy.Configure the Basic Information.
- For the Policy Type, select Data in Motion.Enter a descriptive Name for the Endpoint DLP policy rule.(Optional) Enter a Description to describe the Endpoint DLP policy rule.Select the Severity of the Enterprise DLP incident when sensitive data is moved between an endpoint and a peripheral device.Enable Policy is enabled by default and enables the Endpoint DLP policy rule after you save.Disable this setting if you don't want to immediately enable the Endpoint DLP policy rule after creation.Click Next to continue.Configure the policy rule Classifiers to define the match criteria.
- Select the Data Profile that contains the match criteria you want to inspect for and block. You can select a predefined or custom data profile.Select the File Types you want the Endpoint DLP policy rule to apply to.You can select Any File Types (default) to inspect all supported file types moved between an endpoint and the peripheral device.Configure the Scope to define which users and peripheral devices the policy rule applies to.For Enterprise DLP to take the configured Response action, both Users and Peripherals must be matched.
- Select the Users the policy rule applies to.
- Any Users & GroupsCreate a peripheral control policy rule that applies to all users. Additionally, you can Exclude one or more users from the peripheral control policy rule.
- Select Users & GroupsCreate a peripheral control policy rule that applies to specific users and groups. You can configure the policy rule to apply to either specific users or user groups, or to both.Include
- Select Users—Select one or more specific users to which the rule applies.
- Select Groups—Select one or more user groups to which the rule applies.
Exclude—Select one or more users to exclude from the peripheral control policy group. You must select at least one user group in order to exclude one or more users.
Select the Peripherals you want to inspect and block file movement to if sensitive data is detected.You can add USB devices, printers, and network shares in a single data in motion policy rule. The list of included devices for each type of peripheral device are independent of each other and can be configured as needed. For example, you can create a policy rule that includes no USB devices, all printers, and only specific network shares you selected.- Any (default)—Policy rule applies all USB, printer, or network share peripherals added to Enterprise DLP.
- Select— Policy Rule applies only to the selected peripheral devices or peripheral groups.
- None—Policy rule doesn't apply to any USB, printer, or network share peripherals added to Enterprise DLP.
Click Next to continue.Configure the Response to define the action Enterprise DLP takes when sensitive data is detected.- Action—Action Enterprise DLP takes if a User accesses a Peripheral device defined in the policy rule Scope.
- Incident Assignee—The administrator the Enterprise DLP incident is assigned to if one is generated against the policy rule.
- Email Notifications—Add additional administrators to send email notifications when an incident is generated against the policy rule.
Click Next to continue.Define the Evaluation Priority for the peripheral control policy rule in your Endpoint DLP policy rulebase.You can use the Priority Selection to quickly insert the peripheral control policy rule in the appropriate location in your policy rulebase hierarchy.click Next to continue.Review the policy rule Summary to verify its configured correctly and Save.Push your Endpoint Policy rule.- Select Push Policies and Push Policies.(Optional) Enter a Description for the Endpoint DLP policy push.Review the Push Policies scope to understand which Endpoint DLP policy rules and peripheral group configuration changes are included in the push.Push.Review your Endpoint DLP Audit and Push Logs.Review your Enterprise DLP Incidents.A DLP incident is generated when a user moves a file from the endpoint to the peripheral device but sensitive data is detected and the file move is blocked because sensitive data was detected.(Block policy rule for USB and Network Share Peripherals on macOS only) The Prisma Access Agent automatically moves a blocked file to the following local folder on the endpoint for quarantine for 90 days when Endpoint DLP detects and blocks a file containing sensitive data. The Prisma Access Agent automatically deletes the file from the endpoint after 90 days./Library/Application Support/PaloAltoNetworks/DLP/quarantine/This applies to all file movement operations available on macOS. Navigate to the local folder on the endpoint and move the file to a different folder on the endpoint to recover the file.