Prepare the VM-Series Firewall Image for Cisco ENCS
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable ZRAM on the VM-Series Firewall
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Install a License API Key
- Use Panorama-Based Software Firewall License Management
-
- Maximum Limits Based on Memory
- Activate Credits
- Create a Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a FW-Flex License
- Transfer Credits
- Renew Your Software NGFW Credit License
- Deactivate License (Software NGFW Credits)
- Create and Apply a Subscription-Only Auth Code
- Migrate to a Flexible VM-Series License
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
-
-
- VM-Series Firewall for NSX-V Deployment Checklist
- Install the VMware NSX Plugin
- Apply Security Policies to the VM-Series Firewall
- Steer Traffic from Guests that are not Running VMware Tools
- Dynamically Quarantine Infected Guests
- Migrate Operations-Centric Configuration to Security-Centric Configuration
- Add a New Host to Your NSX-V Deployment
- Use Case: Shared Compute Infrastructure and Shared Security Policies
- Use Case: Shared Security Policies on Dedicated Compute Infrastructure
- Dynamic Address Groups—Information Relay from NSX-V Manager to Panorama
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
- Use Migration Coordinator to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
-
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
-
- What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
- How Does the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1) Enable Dynamic Scaling?
- Plan the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1)
- Customize the Firewall Template Before Launch (v2.0 and v2.1)
- Launch the VM-Series Auto Scaling Template for AWS (v2.0)
- SQS Messaging Between the Application Template and Firewall Template
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.0)
- Modify Administrative Account and Update Stack (v2.0)
-
- Launch the Firewall Template (v2.1)
- Launch the Application Template (v2.1)
- Create a Custom Amazon Machine Image (v2.1)
- VM-Series Auto Scaling Template Cleanup (v2.1)
- SQS Messaging Between the Application Template and Firewall Template (v2.1)
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.1)
- Modify Administrative Account (v2.1)
- Change Scaling Parameters and CloudWatch Metrics (v2.1)
-
-
- Enable the Use of a SCSI Controller
- Verify PCI-ID for Ordering of Network Interfaces on the VM-Series Firewall
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Enable Azure Application Insights on the VM-Series Firewall
- Set up Active/Passive HA on Azure
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
End-of-Life (EoL)
Prepare the VM-Series Firewall Image for Cisco ENCS
Download or create the files necessary to convert the
PAN-OS qcow2 file, and convert the file to a Cisco ENCS image.
You can convert a PAN-OS qcow2 file from the
NFVIS graphical user interface or the command line interface.
Convert a qcow2 File from the Graphical User Interface
- In NFVIS, go to VM Life CycleImage RepositoryImage Packaging.
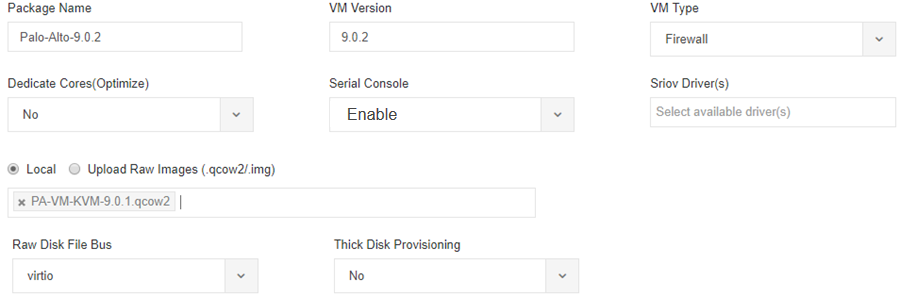
- Fill in
the package information as shown below, supplying your own values.
- Enter a Package Name and VM Version, and for the VM Type, choose Firewall.
- Enable the Serial Console.
- Leave the Sriov Driver(s) field blank, as SR-IOV is not supported.
- Select Local to choose a qcow2 file you uploaded previously, or click Upload Raw Images to upload a qcow2 file.
- Log in to the Palo Alto Networks Customer Support Portal.If you have not already done so, create a support account and register the VM-Series firewall.
- Select SupportSoftware Updates and from the Filter By drop-down, select Pan OS for VM-Series KVM Base Image, for example, version 9.1.
- Download the qcow2 image.
![]()
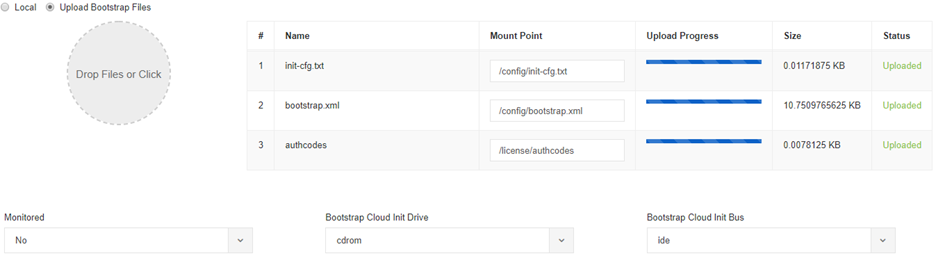
- Upload the bootstrap files.
![]()
- Set the Advanced Configuration.
![]()
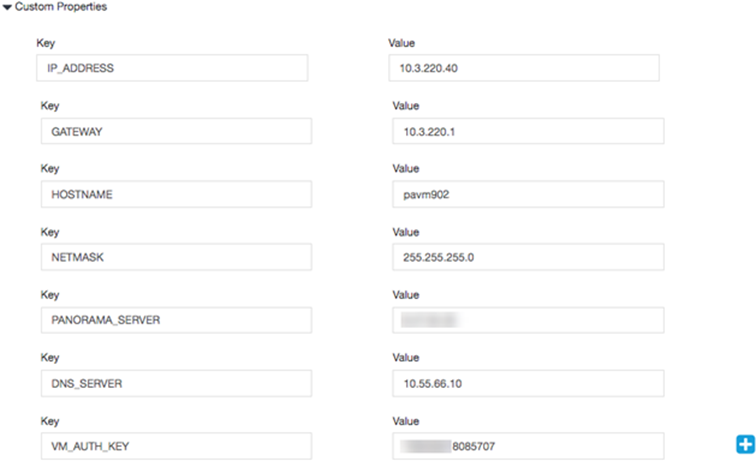
- Enter values for Custom Properties.
![]()
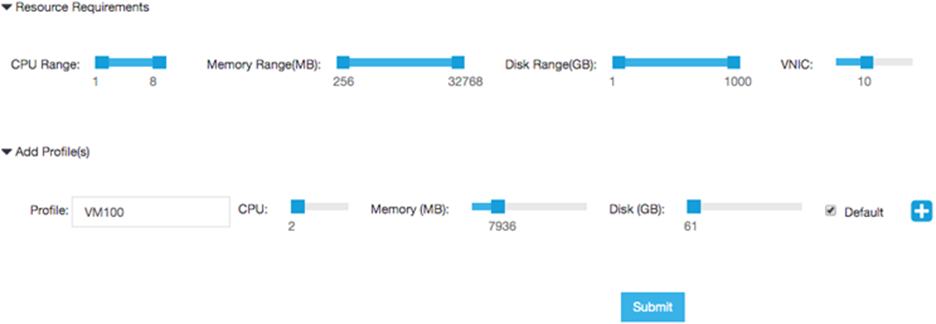
- Set values for your resource requirements and choose
the Default profile, or add a profile for the current configuration.Click Submit to save your package.
![]()
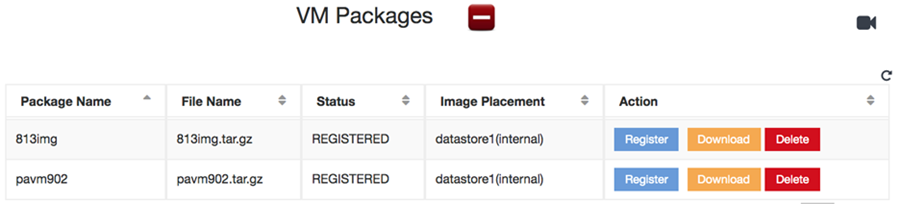
- Click Register to register the
new image.
![]()
Convert a qcow2 File from the Command Line Interface
To create a bootstrap file from the command
line interface, you create the file image_properties_template.xml then
use the using the VM Image Packaging utility to
create a .tar file, which you convert using
the nfvpt.py script. The output is a tar.gz file
that can be uploaded from the NFVIS user interface.
- Create or choose a folder on your local machine (the conversion folder) in which you want to download and save the files necessary to convert the VM-Series firewall qcow2 image to the Cisco ENCS format.
- Obtain
the VM-Series firewall qcow2 image.
- Log in to the Palo Alto Networks Customer Support Portal.If you have not already done so, create a support account and register the VM-Series firewall.
- Select SupportSoftware Updates and from the Filter By drop-down, select Pan OS for VM-Series KVM Base Image, for example, version 9.1.
- Download the qcow2 image to the conversion folder.
- Log in to the Palo Alto Networks Customer Support Portal.
- Create
the following init-cfg.txt file
in the conversion folder.
type=static ip-address=${IP_ADDRESS} default-gateway=${GATEWAY} netmask=${NETMASK} ipv6-address= ipv6-default-gateway= hostname=${HOSTNAME} vm-auth-key=${VM_AUTH_KEY} panorama-server=${PANORAMA_SERVER} panorama-server-2= tplname= dgname= dns-primary=${DNS_SERVER} dns-secondary= op-command-modes=jumbo-frame, mgmt-interface-swap** dhcp-send-hostname=yes dhcp-send-client-id=yes dhcp-accept-server-hostname=yes dhcp-accept-server-domain=yes - Create a text file named authcodes (no extension), and enter the auth codes for the VM-Series firewall capacity and subscriptions. Save the file in the conversion folder.
- Create
the following image_properties_template.xml file
in the conversion folder, and supply values for your deployment:
<image_properties> <vnf_type>FIREWALL</vnf_type> <name>pafw</name> <version>9.1.0</version> <bootup_time>-1</bootup_time> <root_file_disk_bus>virtio</root_file_disk_bus> <root_image_disk_format>qcow2</root_image_disk_format> <vcpu_min>2</vcpu_min> <vcpu_max>8</vcpu_max> <memory_mb_min>4096</memory_mb_min> <memory_mb_max>16384</memory_mb_max> <vnic_max>8</vnic_max> <root_disk_gb_min>32</root_disk_gb_min> <root_disk_gb_max>60</root_disk_gb_max> <console_type_serial>true</console_type_serial> <sriov_supported>true</sriov_supported> <pcie_supported>false</pcie_supported> <monitoring_supported>false</monitoring_supported> <monitoring_methods>ICMPPing</monitoring_methods> <low_latency>true</low_latency> <privileged_vm>true</privileged_vm> <custom_property> <HOSTNAME> </HOSTNAME> </custom_property> <custom_property> <IP_ADDRESS> </IP_ADDRESS> </custom_property> <custom_property> <NETMASK> </NETMASK> </custom_property> <custom_property> <GATEWAY> </GATEWAY> </custom_property> <custom_property> <PANORAMA_SERVER> </PANORAMA_SERVER> </custom_property> <custom_property> <DNS_SERVER> </DNS_SERVER> </custom_property> <custom_property> <VM_AUTH_KEY> </VM_AUTH_KEY> </custom_property> <default_profile>VM-50</default_profile> <profiles> <profile> <name>VM-50</name> <description>VM-50 profile</description> <vcpus>2</vcpus> <memory_mb>5120</memory_mb> <root_disk_mb>60000</root_disk_mb> </profile> <profile> <name>VM-100-n-200</name> <description>VM-100 and VM-200 profile</description> <vcpus>2</vcpus> <memory_mb>7168</memory_mb> <root_disk_mb>60000</root_disk_mb> </profile> <profile> <name>VM-300</name> <description>VM-300 profile</description> <vcpus>2</vcpus> <memory_mb>9216</memory_mb> <root_disk_mb>60000</root_disk_mb> </profile> <profile> <name>VM-1000-HV</name> <description>VM-1000-HV profile</description> <vcpus>4</vcpus> <memory_mb>9216</memory_mb> <root_disk_mb>60000</root_disk_mb> </profile> <profile> <name>VM-500</name> <description>VM-500 profile</description> <vcpus>4</vcpus> <memory_mb>16384</memory_mb> <root_disk_mb>60000</root_disk_mb> </profile> </profiles> <cdrom>true</cdrom> <bootstrap_file_1>/config/init-cfg.txt</bootstrap_file_1> <bootstrap_file_2>/config/bootstrap.xml</bootstrap_file_2> <bootstrap_file_3>/license/authcodes</bootstrap_file_3> </image_properties> - Download the image packaging utility.
- Log in to the Enterprise NFVIS user interface and select VM Life Cycle Image Repository.
- Click the Browse Datastore tab, and navigate to dataintdatastoreuploadsvmpackagingutility.
- Download nfvisvmpackagingtool.tar to the conversion folder.
- Untar the file:
tar -xvf nfvisvmpackagingtool.tar
- In the conversion folder that contains the qcow2, the init-config.txt and
the authcodes file, run the nfvpt.py script.
See the nfvpt.py image packaging utility documentation.The following sample creates the image file Palo-Alto-9.1.0, and a VM-100 profile. Options are space-separated (the sample shows options on separate lines for clarity only) and custom options are key-value pairs with a colon separator.
./nfvpt.py -o Palo-Alto-9.1.0 -i PA-VM-KVM-9.1.0.qcow2 -n PAN902 -t FIREWALL -r 9.1.0 --monitored false --privileged true --bootstrap /config/init-cfg.txt:init-cfg.txt,/license/authcodes:authcodes --min_vcpu 2 --max_vcpu 8 --min_mem 4096 --max_mem 16384 --min_disk 10 --max_disk 70 --vnic_max 8 --optimize true --console_type_serial true --profile VM-100,"VM-100 profile",2,7168,61440 --default_profile VM-100 --custom HOSTNAME:hello --custom IP_ADDRESS:10.2.218.24 --custom NETMASK:255.255.255.0 --custom GATEWAY:10.2.218.1 --custom DNS_SERVER:10.55.66.10 --custom PANORAMA_SERVER:0.10.10.0 --custom VM_AUTH_KEY:123451234512345
- Upload the converted image.
- In the NFVIS user interface, select VM Life Cycle Image Repository and click the blue Images icon to show the Drop Files or Click circle.
- Drag the converted file into the circle, or click to browse and select your file.
- In the Status column, click Start. When the upload is complete, the image is registered, and the file you uploaded displays in the Image Registration tab Images list.