Strata Cloud Manager
Configuration: Security Posture Settings
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
Configuration: Security Posture Settings
Customize security posture checks for your deployment to maximize relevant
recommendations.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
→ The features and capabilities available to you in Strata Cloud Manager depend on which license(s) you are
using.
|
Strata Cloud Manager now organizes Security Posture Settings under the Unified
Incident Framework to deliver a unified and contextual incident management
experience. Previously, you could access the security posture check from
Configuration > Posture > Settings. With the unified incident framework, these
security posture settings have moved to Incidents > Settings. This update
aligns all posture-related rules and custom checks with incident workflows,
enabling easier correlation between configuration issues and the incidents they
generate.
Strata Cloud Manager leverages a set of predefined Best Practice Checks that align
with industry-specific standard cybersecurity controls, such as CIS (Center for
Internet Security), and NIST (National Institute of Standards and Technology) and
custom checks you create based on the specific needs of your organization. These
checks evaluate configurations and settings within the cloud infrastructure,
identifying deviations from best practices or compliance requirements.
The security posture checks in Strata Cloud Manager encompass a range of
security domains, including network security, data protection, and identity and
access management. These checks assess firewall rules, encryption, authentication
mechanisms, and the overall integrity of configurations.
When your configuration detects deviations, Strata Cloud Manager provides
actionable insights and remediation recommendations, and can even automate some
parts of the process for correcting misconfigurations and noncompliant settings to
help you maintain a secure and compliant cloud environment with minimal manual
intervention.
Security posture settings bring together the functionality of both the AIOps and
Strata Cloud Manager security check settings pages.
Select Configuration PostureSettings to view, manage, and customize security posture checks for your
deployment to maximize relevant recommendations.
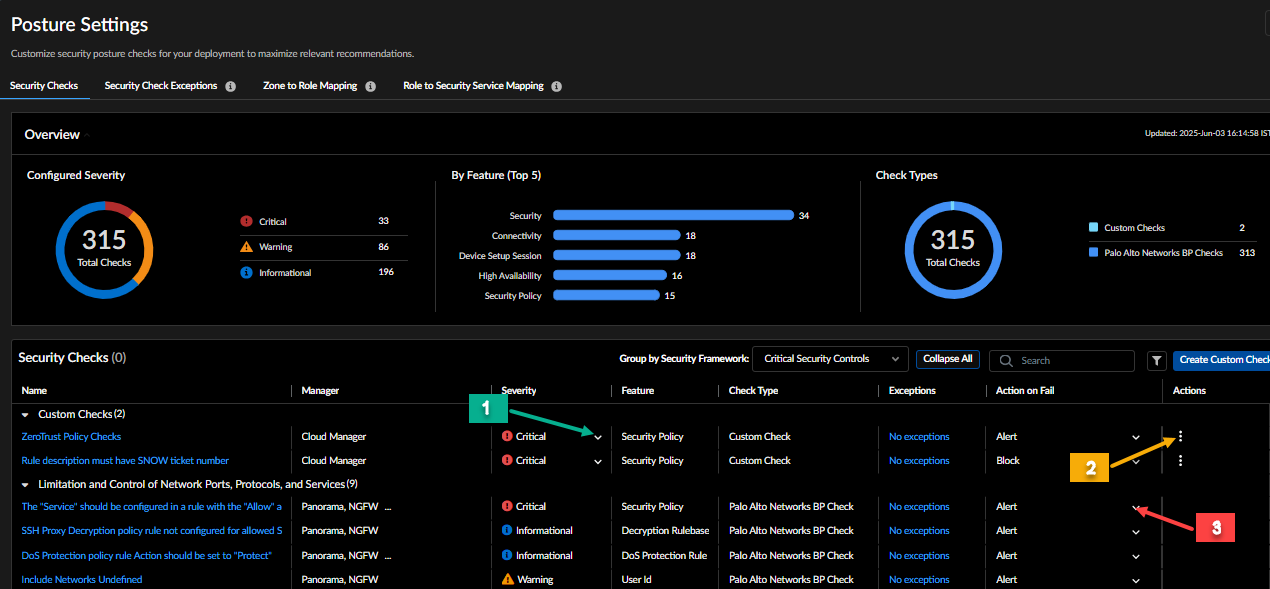
- Security Checks – List of the best practice checks that are used to evaluate your configuration.Your configuration is compared against these checks to assess the security posture of your devices and to generate security alerts. You can perform the following actions to manage these checks based on your environment:
- Set the severity level for your custom checks to identify the checks that are the most critical to your deployment.You can change the severity level for your custom checks, but the severity levels for Palo Alto Networks Best Practice Checks are fixed and can't be changed.
- Create and delete your own custom checks, clone and edit existing checks to
create new ones, and make special exceptions for
checks that you don't want applied to portions of your deployment.As part of the initial rollout of these checks, you can clone checks that are in the custom check framework.
- Set the response when a check fails.
- Alert (default)—Raises an alert for the failed check.
- Block—Stop potential misconfigurations before they enter your deployment. Block can mean any of the following depending on how you manage it:
- Inline Checks on Strata Cloud Manager—Prevents you from committing or pushing a noncompliant configuration, but won't prevent you from saving your configuration locally.
- Real-Time* Inline Checks on Strata Cloud Manager—Prevents you from even saving a noncompliant configuration.
- Panorama Managed**—Prevents you from committing a noncompliant configuration to Panorama but won't prevent you from saving it to the Panorama candidate configuration.
- PAN-OS Web Interface, API, or CLI management—Block has no enforcement effect on configurations that are not either managed by Strata Cloud Manager or Panorama.
- *Due to their logical complexity, some inline checks are run asynchronously on a fixed schedule but not in real time. A failure of a real-time check in your configuration will prevent you from saving that configuration, even locally.
- **The Panorama CloudConnector Plugin is required to enforce the block commit action on Panorama.
![]()
- Security Check ExceptionsTurn off individual checks for devices or groups of devices you specify.
- Zone to Role MappingMap the zones in NGFWs to roles to get customized recommendations.
- Role-to-Security Service MappingManage the security services needed for traffic between zones and roles in all NGFWs.
Create a Custom Check
Create your own custom check from an existing check. Alternatively, skip to step
#4 to create a custom check from scratch.
With the unified incident framework, the
security posture settings have moved to Incidents > Settings. This
update aligns all posture-related rules and custom checks with incident
workflows, enabling easier correlation between configuration issues and the
incidents they generate.
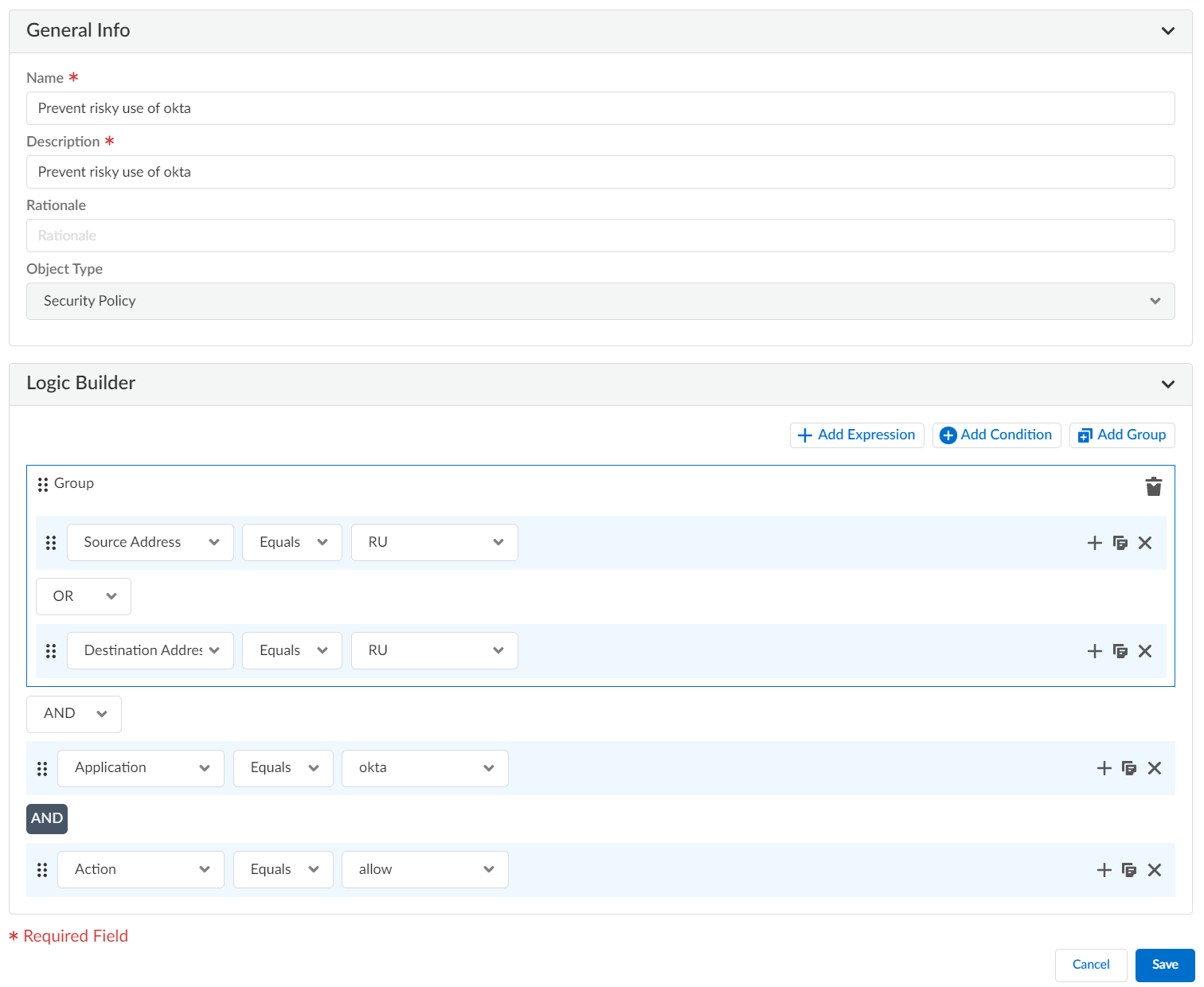
- Select ConfigurationPostureSettings.Identify the check you want to clone and Clone.Edit the check you cloned and skip to step #5 to make your changes.Go to ConfigurationPostureSettings, and select Create Custom Check.Specify the General Information for your check. Your custom check must have a Name and a Description, but you should also add a Recommendation and a Rationale for your check to help others understand the intent of and best practice for your custom check.Optional Select an Object Type– the section of your configuration for which you're creating a check that determines which Rule Properties to Match you can choose when creating your check.Use the Logic Builder for your custom check.
- Add Expression–A single line of logic that describes the match criteria for a configuration.
Rule Properties to Match Match Operator Specific Criteria - General–Name, Description, Position, and Schedule
- Sources–Zones, addresses, Users
- Destinations–Zones and addresses
- Applications, Services, and URLs
- Actions and Advanced Inspection
- Is
- Is not
- Is empty
- Is not empty
- Starts with
- Ends with
- Contains
- Greater than
- In
- Is equal or greater than
- Is equal or less than
- Less than
- Equal
- Not equal
- Does not contain
- All of
- Some of
- None of
[Text field] Add Condition–Use logical operators (such as AND, OR, IF, THEN, ELSE, and ELSE IF) to connect or combine expressions, additional conditions, and groups.Add Group–Create a set of expressions, conditions, or both. This group, taken together, results in a True or False condition.- Adds a new expression or condition
![]()
- Clones an expression or condition
![]()
- Removes an expression or condition
![]()
The expression in this example issues a warning when it sees policy rules that allow Okta traffic to and from Russian IP addresses. The example simply illustrates how the logic builder works, and isn't intended to be a recommendation.![]() Save your check.
Save your check.Manage Your Checks
You can perform any of the following Actions on your security checks:- Clone*–Creates a copy of a check.
- Edit**–Make changes to an existing custom check.
- Delete**–Removes a custom check you created.
Select the checks you want to take action on and select the appropriate action.- *You can clone only one check at a time.
- **You can edit or delete custom checks only.
- You may need to get permission from an administrator to edit a custom check.
Create an Exception for a Check
Where needed, you can restrict where checks are applied in your deployment.- Select ConfigurationPostureSettingsSecurity Check Exceptions and Create Security Check Exception.Alternatively, Select Configuration PostureSettings, and identify the check you want to exclude and select it (Exceptions column).Specify the information needed to Create Exception Rule for your check. Provide a name, a reason, and conditions for your exception.The Security Check Exception feature is currently only applicable to alerts, and the Best Practices and Security Posture Insights dashboards.Optional Add a Ticket Number or a Description for your exception to help others understand the intent and history behind for your exception.Save your exception.
Your Checks at Work
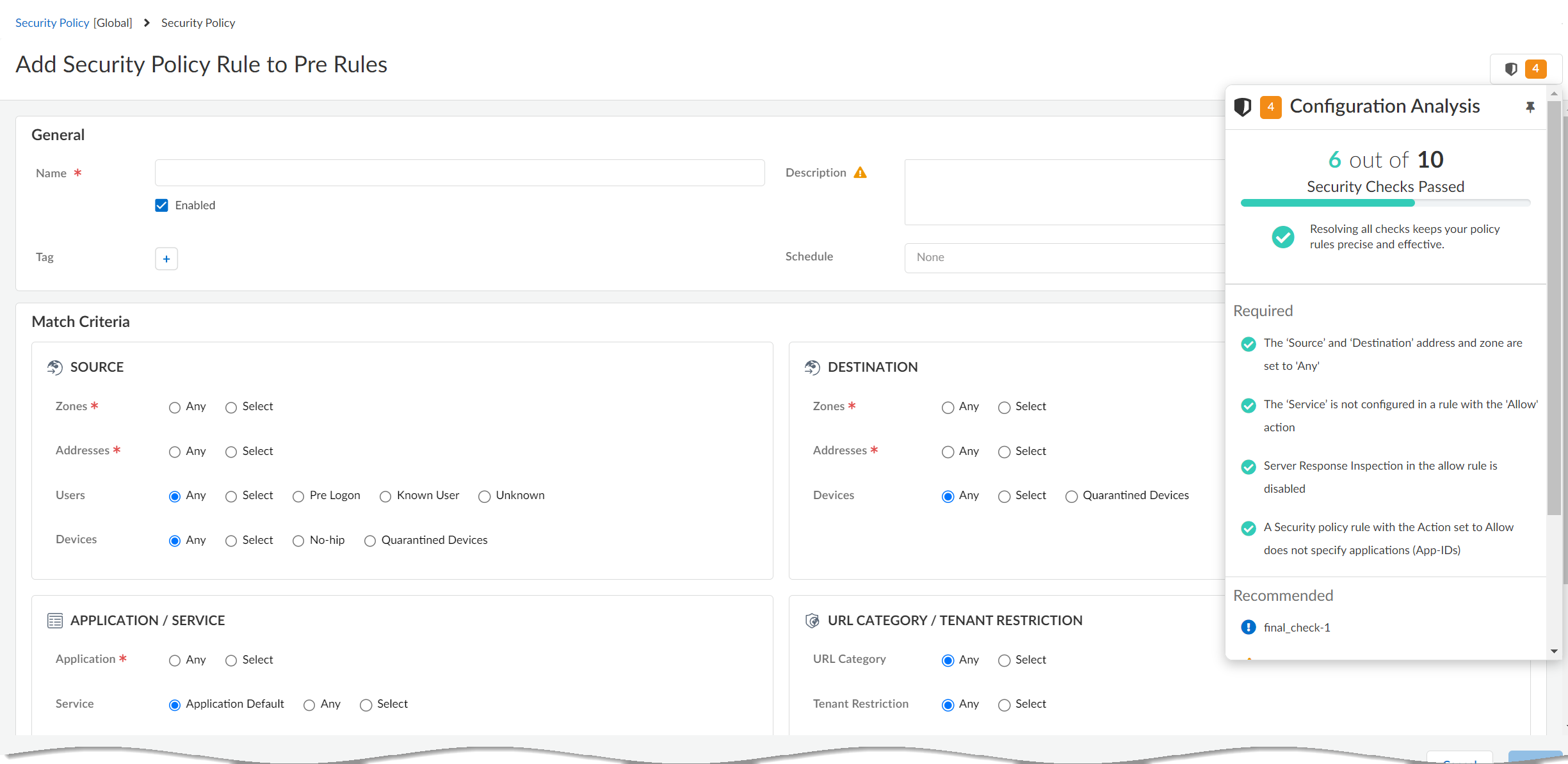
Field-level checks show you where your configuration does not align with a best practice or custom check. The checks provide best practice guidance inline, so that you can immediately take action.You can also view and manage security checks right where you are.- Create and manage your policy
rules–Security policy rules allow you to enforce rules and
take action, and can be as general or specific as needed. (ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy)
![]()
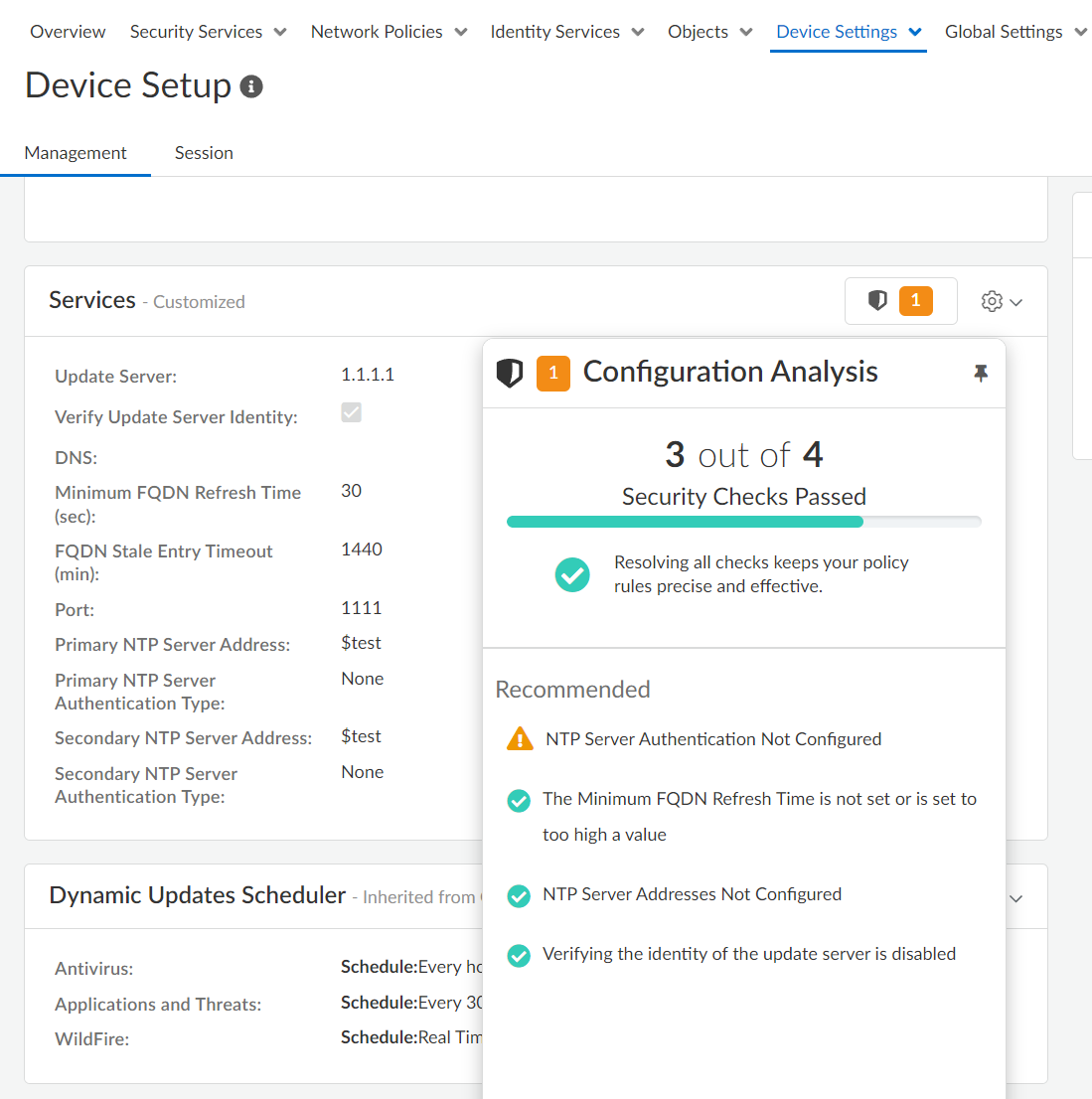
- Setup Devices–Configure
service route, connection settings, allowed services, and administrative
access settings for the management and auxiliary interfaces for your
firewalls. (ConfigurationNGFW and Prisma AccessDevice SettingsDevice Setup)
![]()
If the configuration you're trying to save does not pass your criteria to pass, you will have the option to remediate the issue, or override* the warning and save your changes anyway.- *Override permission is governed by role-based access controls (RBAC) and must be enabled for your role for this option to appear. Actions pertaining to overrides, custom checks, and exceptions, are logged in Audit Logs:Log ViewerAudit (log type).
- Everything you do with custom checks, overrides, and exceptions is logged in Audit: Log ViewerAudit (log type).