Download PDF
GlobalProtect
Resolve FIPS-CC Mode Issues
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
Resolve FIPS-CC Mode Issues
View possible FIPS-CC mode issues and the corresponding
solutions.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
NGFW (managed by Panorama)
|
|
The following section describes possible
FIPS-CC mode issues and the corresponding solutions. If you encounter
any issues that are not described below, please contact your GlobalProtect™
administrator for troubleshooting assistance.
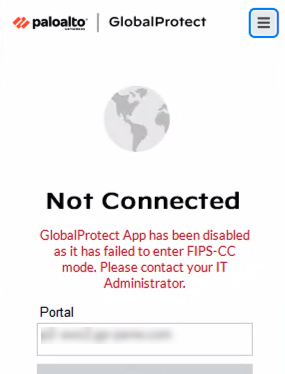
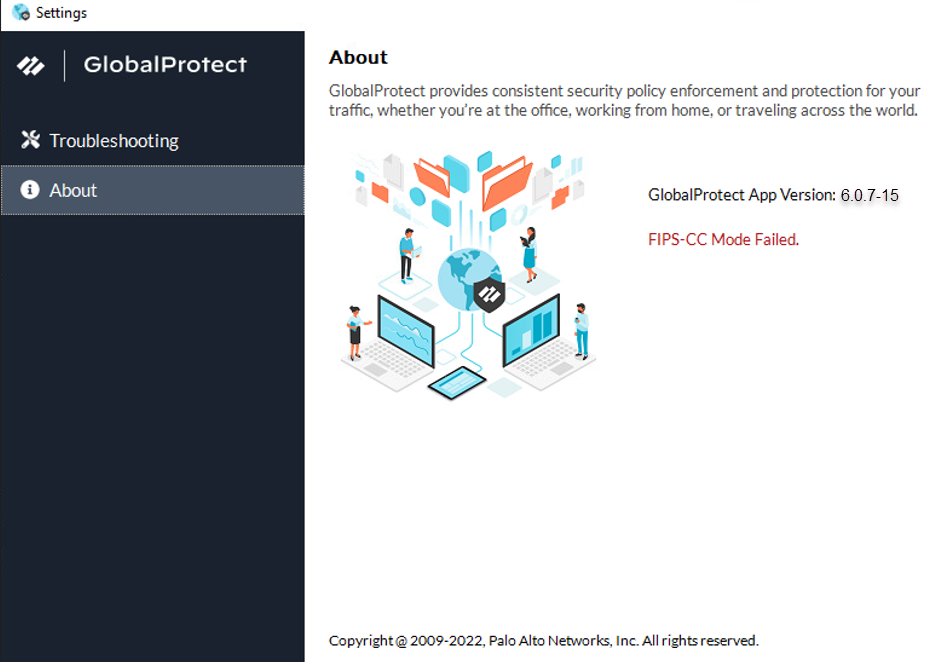
- Issue:The GlobalProtect app fails to initialize in FIPS-CC mode due to a FIPS Power-On Self-Test (POST) or integrity test failure.
- Description: After you enable FIPS-CC mode, the GlobalProtect app performs FIPS Power-On Self-Tests (POST) and integrity tests during app initialization and system or app reboots. If either of these tests fail, the GlobalProtect app is disabled and the About window displays the FIPS-CC Mode Failed error message:
![]()
![]()
- Resolution: Restart the app to clear the error condition. If the issue persists, uninstall and then reinstall the app.
- Issue:The GlobalProtect app is unable to establish a connection in FIPS-CC mode due to a FIPS conditional self-test failure.
- Description: After the GlobalProtect app initializes in FIPS-CC mode, it performs FIPS conditional self-tests. If the self-tests fail, the GlobalProtect app terminates the session and remains disconnected.
- Resolution: To establish a GlobalProtect connection, you must re-authenticate to the GlobalProtect portal and enable FIPS-CC mode again.
If GlobalProtect is unable to initialize or connect in
FIPS-CC mode, you can access the Troubleshooting tab
of the GlobalProtect Settings panel to view and collect logs for
troubleshooting. All other tabs are unavailable until GlobalProtect
connects successfully.
The following tables list
the error messages displayed when certificate validation fails for
Windows and macOS platforms. Administrators can view the error messages
for troubleshooting and resolving the issues.
FIPS-CC Certification Validation | Error Messages |
|---|---|
Trusted root CA certificate not found. | Failed validation of the X.509v3 certificate:
The portal certificate is not signed by a trusted certificate authority. |
CA certificate expired. | Failed validation of the X.509v3 certificate:
The portal certificate is not within its validity period. |
CA certificate revoked. | Failed validation of the X509v3 certificate.
Certificate revoked. |
CA certificate BasicConstraints cA flag
not found. | Windows: Failed validation of the X.509v3 certificate. CA certificate
basicConstraints flag not found or invalid.
macOS: Basic Constraints extension
required per policy, but not present. |
CA certificate BasicConstraints cA flag
set to ‘False’. | BasicConstraintsCA = 0;StatusCodes = ("-2147408893") |
EC Explicit Parameter missing. | FIPS-CC error: Non compliant FIPS-CC mode
certificate. ECDSA cert with Explicit EC parameters. |
Intermediate CA with basic constraints missing. | Windows: Failed validation of the X.509v3 certificate. CA certificate
basicConstraints flag not found or invalid.
macOS: Basic Constraints extension
required per policy, but not present. |
CA certificate with no CA Signing purpose
in intermediate. | Windows: Failed validation of the X509v3 certificate. CA certificate
basicConstraints flag not found or invalid.
macOS: Invalid Key Usage for policy. |
CA certificate with no CA Signing purpose
in root. | Windows: Failed validation of the X.509v3 certificate. Missing caSigning
field in the CA chain.
macOS: Failed validation of the X.509v3
certificate. Trusted Root CA certificate not found. KeyUsage =
0;StatusCodes = ("-2147408890") |
Certificate validation for revoked certificate. | Failed validation of the X.509v3 certificate:
The certificate is not fips compliant. Please access the system
logs for more information. |
Certificate validation with certificate
without cRLsign key usage bit set. | Failed validation of the X.509v3 certificate.
Missing CRL Sign purpose in the (Extended) KeyUsage field. |
Certificate (OCSP) validation for revoked GlobalProtect
client certificate. | Connection Failed: A valid certificate is
required for authentication. If the issue persists, contact your administrator. |
Certificate (OCSP) validation for certificate
missing OCSP signing purpose. | Failed validation of the X.509v3 OCSP signing
certificate. Missing Extended Key Usage field. |
Certificate validation with OCSP when the
server is unreachable. | Failed validation of the X509v3 certificate.
Read/Access OCSP or CRL failed. |
| Server Certificate Validation | Error Messages |
|---|---|
Supported SHA-256, SHA-384, and SHA-512
only. Connection fails if any other algorithm is used (e.g. MD5). Certificates
with SHA-1 are not allowed. | Failed to pre-login to the <portal> with
return value 0(0). |
RSA Key: Failure when length is less than
2048 | Failed to pre-login to the <portal> with
return value 0(0). |
ECDSA Key: Failure when length is not P-256/384/521. | Failed to pre-login to the <portal> with
return value 0(0). |
RSA key exponent failure. | Windows: FIPS-CC error: Non-compliant FIPS-CC mode certificate.
macOS:
CSSMERR_CSP_UNSUPPORTED_KEY_SIZE |
Server certificate expired. | Failed validation of the X.509v3 certificate:
The portal certificate is not within its validity period. |
Server certificate (OCSP) revoked. | Failed validation of the X509v3 certificate.
Certificate revoked. |
Connection failure when Extended Key Usage
field is missing in server certificate. | Failed to pre-login to the <portal> with
return value 0(0). |
Connection failure when Server Authentication
purpose is missing in the Extended key Used field. | Failed to pre-login to the <portal> with
return value 0(0). |
The following tables list the error messages displayed when
certificate validation fails for the iOS platform. In some cases, the error messages
displayed are slightly different from the expected error messages as listed out in the
table. Administrators can view the error messages for troubleshooting and resolving the
issues.
| FIPS-CC Certification Validation |
Error Messages Displayed
|
|---|---|
|
Key Usage missing CA Signing purpose.
|
Unable to build chain to root certificate.
|
|
RSA Key: Failure when length is less than 2048.
|
One or more certificates is using a weak signature algorithm.
|
|
RSA Key -Failure when 1024 bit server certificate is used.
|
One or more certificates is using a weak key size.
|
|
Missing Extended Key Usage field.
|
Failed validation of the X.509v3 certificate. Missing Extended
Key Usage field.
|
|
Verifying server certificate must have serverAuth in EKU.
|
Policy requirements not met.
|
|
Verifying client certificate must have clientAuth in EKU.
|
Failed validation of the X.509v3 certificate. CA certificate 'CA
Signing' is absent but basicConstraints may or may not be
valid.
|
|
Certification path leads to an untrusted root or any CA
certificate in the path has expired or revoked.
|
Failed validation of the X509v3 certificate. Trusted Root CA
certificate not found.
|
|
Basic Constraints missing
|
Failed validation of the X509v3 certificate. Trusted Root CA
certificate not found.
|
|
CA certificate basicConstraints flag not set to True.
|
Unable to build chain to root certificate.
|
|
Certificate Expired
|
One or more certificates have expired or are not valid yet.
|
|
Certificate Revoked
|
One or more certificates have expired or are not valid yet.
|
|
Weak Algorithm Used
|
One or more certificates is using a weak signature algorithm.
|
|
CA signing field missing
|
Policy requirements not met.
|
|
Read/Access for CRL Failed
|
Failed validation of the X509v3 certificate. Read/Access OCSP or
CRL failed.
|
|
Read/Access the OCSP Failed
|
Failed validation of the X509v3 certificate. Read/Access OCSP or
CRL failed.
|
|
OCSP certificate validation failed.
|
Failed validation of the X509v3 certificate. Certificate
revoked.
|
|
Missing OCSP Signing purpose in the ExtendedKeyUsage field.
|
Failed validation of the X.509v3 OCSP signing certificate.
Missing Extended Key Usage field.
|
|
OCSP certificate validation for revoked GlobalProtect client
certificate
|
Failed validation of the X509v3 certificate. Certificate
revoked.
|
|
Certificate revoked - server Certificate (OCSP)
|
Failed validation of the X509v3 certificate. Certificate
revoked.
|