Track Rules Within a Rulebase
Table of Contents
End-of-Life (EoL)
Track Rules Within a Rulebase
To keep track of rules within a rulebase,
you can refer to the rule number, which changes depending
on the order of a rule in the rulebase. The rule number determines
the order in which the firewall applies the rule.
The universally
unique identifier (UUID) for a rule never changes even if
you modify the rule, such as when you change the rule name. The
UUID allows you to track the rule across rulebases even after you
deleted the rule.
Rule Numbers
The firewall automatically numbers each rule
within a rulebase; when you move or reorder rules, the numbers change
based on the new order. When you filter the list of rules to find
rules that match specific criteria, the firewall display each rule
with its number in the context of the complete set of rules in the
rulebase and its place in the evaluation order.
Panorama independently
numbers pre-rules, post-rules, and default rules. When Panorama
pushes rules to a firewall, the rule numbering reflects the hierarchy
and evaluation order of shared rules, device group pre-rules, firewall
rules, device group post-rules, and default rules. You can Preview
Rules in Panorama to display an ordered list of the
total number of rules on a firewall.
- View the numbered list of rules on the firewall.Select Policies and any rulebase under it. For example, PoliciesSecurity. The left-most column in the table displays the rule number.View the numbered list of rules on Panorama.Select Policies and any rulebase under it. For example, PoliciesSecurityPre-rules.After you push the rules from Panorama, view the complete list of rules with numbers on the firewall.From the web interface on the firewall, select Policies and pick any rulebase under it. For example, select PoliciesSecurity and view the complete set of numbered rules that the firewall will evaluate.
![]()
Rule UUIDs
The universally unique identifier (UUID) for a rule is a 32-character string (based on data such as the network address and the timestamp of creation) that the firewall or Panorama assigns to the rule. The UUID uses the format 8-4-4-4-12 (where 8, 4, and 12 represent the number of unique characters separated by hyphens). UUIDs identify rules for all policy rulebases. You can also use UUIDs to identify applicable rules in the following log types: Traffic, Threat, URL Filtering, WildFire Submission, Data Filtering, GTP, SCTP, Tunnel Inspection, Configuration, and Unified.Using the UUID to search for a rule enables you to locate a specific rule you want to find among thousands of rules that may have similar or identical names. UUIDs also simplify automation and integration for rules in third-party systems (such as ticketing or orchestration) that do not support names.In some cases, you may need to generate new UUIDs for existing rulebases. For example, if you want to export a configuration to another firewall, you need to regenerate the UUIDs for the rules as you import the configuration to ensure there are no duplicate UUIDs. If you regenerate UUIDs, you are no longer able to track those rules using their previous UUIDs and the hit data and app usage data for those rules are reset.The firewall or Panorama assigns UUIDs when you:- Create new rules
- Clone existing rules
- Override the default security rules
- Load a named configuration and regenerate UUIDs
- Load a named configuration containing new rules that are not in the running configuration
- Upgrade the firewall or Panorama to a PAN-OS 9.0 release
When you load a configuration that contains rules with UUIDs, the firewall considers rules to be the same if the rule name, rulebase, and virtual system all match. Panorama considers rules to be the same if the rule name, rulebase, and the device group all match.Keep in mind the following important points for UUIDs:- If you manage firewall policy from Panorama, UUIDs are generated on Panorama and therefore must be pushed from Panorama. If you do not push the configuration from Panorama prior to upgrading the firewalls to PAN-OS 9.0, the firewall upgrade will not succeed because it will not have the UUIDs.
- In addition, if you are upgrading an HA pair, upon upgrade to PAN-OS 9.0, each peer independently assigns UUIDs for each policy rule. Because of this, the peers will show as out of sync until you sync the configuration (DashboardWidgetsSystemHigh AvailabilitySync to peer).
- If you remove an existing high availability (HA) configuration after upgrading to PAN-OS 9.0, you must regenerate the UUIDs on one of the peers (DeviceSetupOperationsLoad named configuration snapshotRegenerate UUIDs for the selected named configuration) and commit the changes to prevent UUID duplication.
- All rules pushed from Panorama will share the same UUID; all rules local to a firewall will have different UUIDs. If you create a rule locally on the firewall after you push the rules from Panorama to the firewalls, the rule you created locally has its own UUID.
- To replace an RMA Panorama, make sure you Retain Rule UUIDs when you load the named Panorama configuration snapshot. If you do not select this option, Panorama removes all previous rule UUIDs from the configuration snapshot and assigns new UUIDs to the rules on Panorama, which means it does not retain information associated with the previous UUIDs, such as the policy rule hit count.
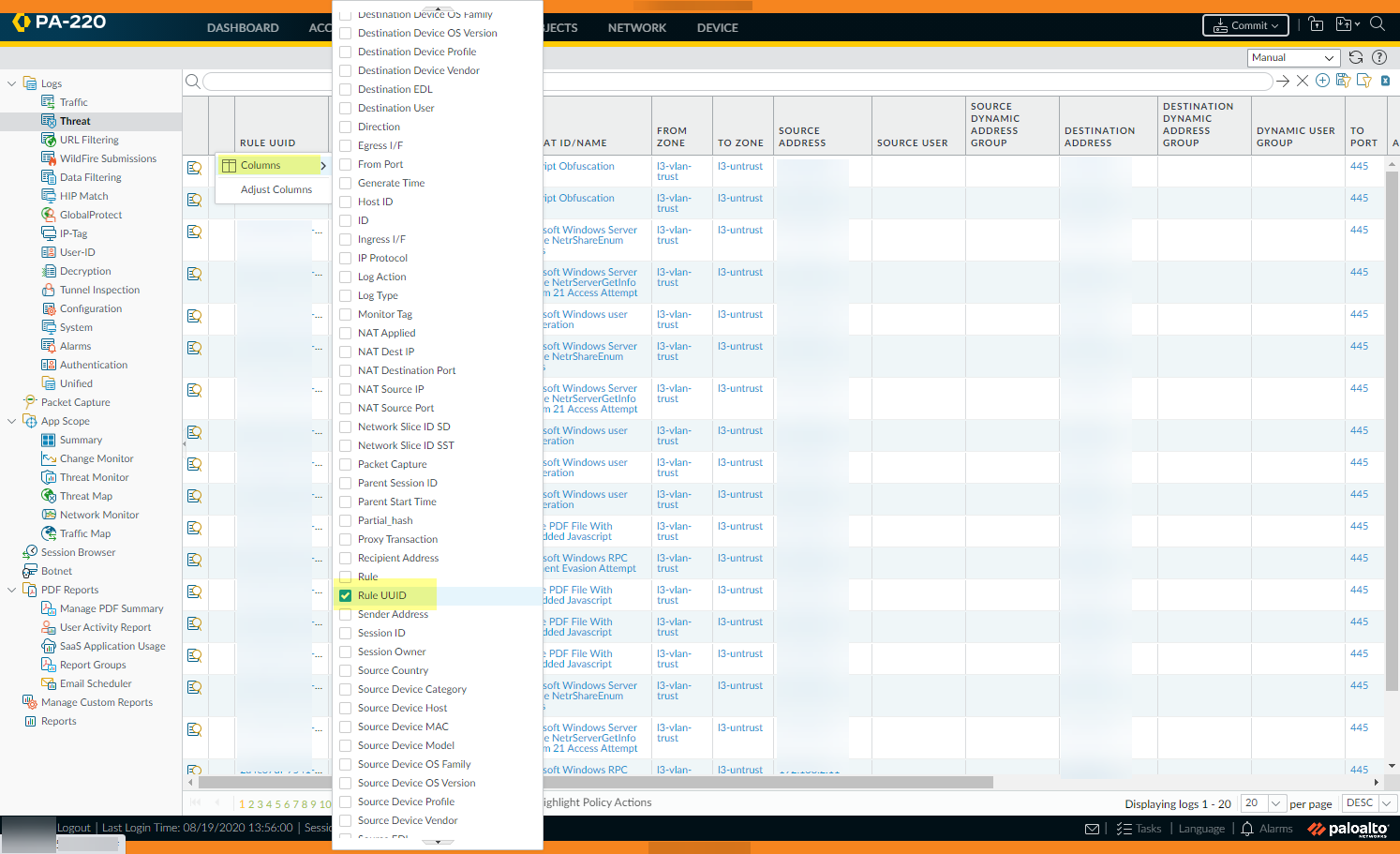
- Display the Rule UUID column for logs and the UUID column for policy rules.To view the UUIDs, you must display the column, which does not display by default.
- To display the UUID in logs:
- Select Monitor and then expand the column
header ().
![]()
- Select Columns.
- Enable Rule UUID.
![]()
- Select Monitor and then expand the column
header (
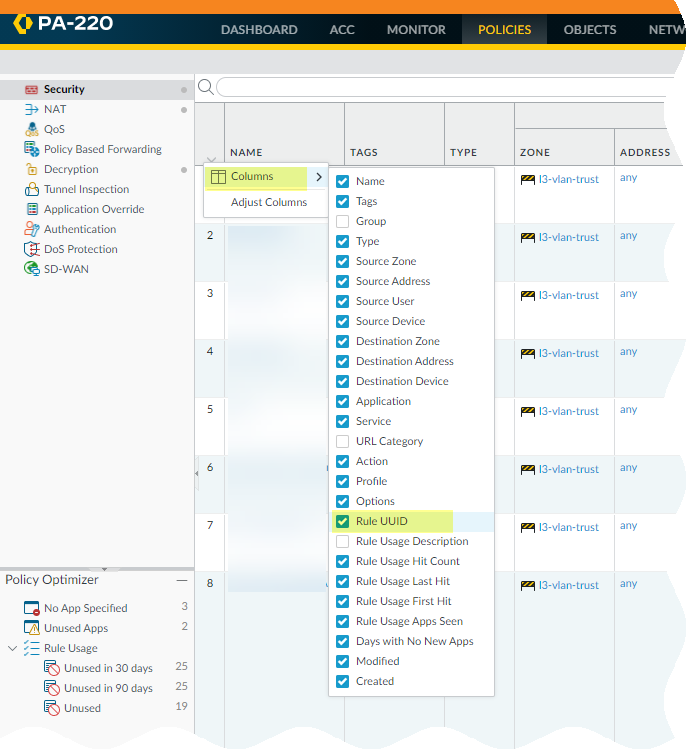
- To display UUIDs on the policy rulebase:
- Select Policies and
then expand the column header ().
![]()
- Select Columns.
- Enable Rule UUID.UUIDs are available for all policy rulebases.
![]()
- Select Policies and
then expand the column header (
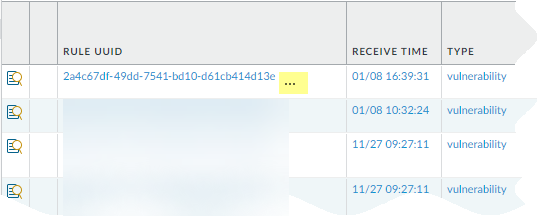
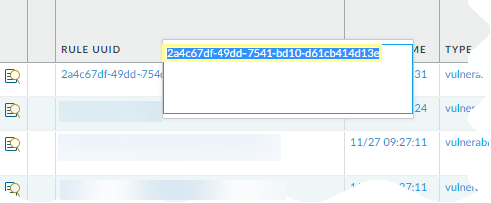
Copy the UUID for a log or policy rule.Copying the UUID allows you to paste the UUID in to searches, the ACC, custom reports, filters, and anywhere else you want to locate a rule identified by that UUID.- Select the ellipses that display when you move your cursor over the entry in the Rule UUID column.
![]() Copy the UUID from the pop-up.
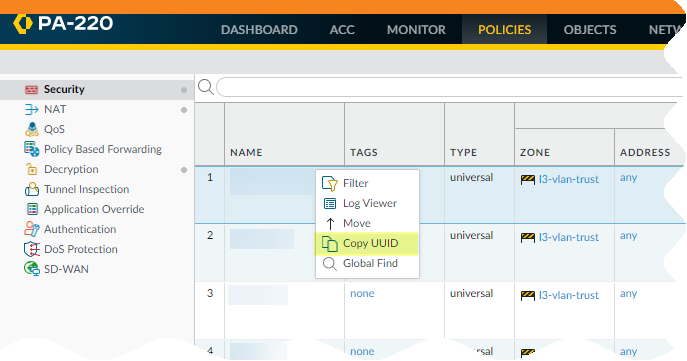
Copy the UUID from the pop-up.![]() You can also go to the Policies tab, click the arrow to the right of the rule name, and Copy UUID.
You can also go to the Policies tab, click the arrow to the right of the rule name, and Copy UUID.![]() Check the Configuration Logs to view UUIDs for deleted rules.To view the UUID for a deleted rule, select MonitorLogsConfiguration.
Check the Configuration Logs to view UUIDs for deleted rules.To view the UUID for a deleted rule, select MonitorLogsConfiguration.
- To display the UUID in logs: