Next-Generation Firewall
Configure TACACS Accounting
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Configure TACACS Accounting
Learn how to configure user accounting for your TACACS+ server.
TACACS+ is designed to use the Authentication, Authorization, and Accounting (AAA)
framework for device administration. Authentication confirms the user's identity
while authorization determines access to resources. To keep track of the services
provided during the user's session, accounting keeps a record of when services were
initiated and terminated, as well as any services in progress.
TACACS+ Accounting can be used as an auditing tool. The TACACS+ accounting records
contain all information used in authorization records, as well as
accounting-specific information such as start and stop times and resource usage
information. There are three types of TACACS+ accounting records:
- Start records to indicate a service is about to begin
- Stop records to indicate termination of the service
- Update records to indicate service is still in progress
The firewall uses the TACACS+ accounting client to communicate with your TACACS+
accounting server using the RFC 8907 protocol for connection and session
establishment with the accounting server as well as the accounting packets that are
sent or received from the server. The TACACS + accounting client uses an accounting
server profile that you select and the server profile can contain more than one
accounting server.
The client selects the first server in the list where it can successfully establish a
connection and receive accounting records. The connection is cached until the client
is unable to send accounting records to the connected accounting server. If the
client cannot connect to the cached server, it attempts to connect to the next
accounting server in the server profile. If the client is unable to connect to any
of the servers in the server profile, it logs the failure as an error.
You can configure a TACACS+ server profile for either
authentication or accounting but you cannot use the same profile for both
authentication and accounting. If you need to use the same TACACS+ server for
accounting and authentication, you must configure two profiles containing the same
server information, then configure one profile for authentication and the second
profile for accounting.
The TACACS+ accounting client supports the following arguments:
| task_id | timezone |
| start_time | event |
| stop_time | reason |
| elapsed_time | err_msg |
If you use TACACS+ for Device Administration, all TACACS+
client devices must be configured to send an accounting start packet for each
command that is entered regardless of how the commands were authorized. The Command
Accounting packet must include the service and
cmd arguments and if necessary, the
cmd-arg arguments described in Section 8.2 of RFC 8907.
- Create a TACACS+ server profile on the firewall or Panorama for each TACACS+ accounting server that you want to include.(Panorama only) Add the TACACS+ server profile to a template or template stack.You only need to complete this step if you want to push the TACACS+ server profile to one or more firewalls. If you only want to configure accounting for TACACS+ for Panorama, you do not need to complete this step.Edit the Accounting Settings depending on your configuration.
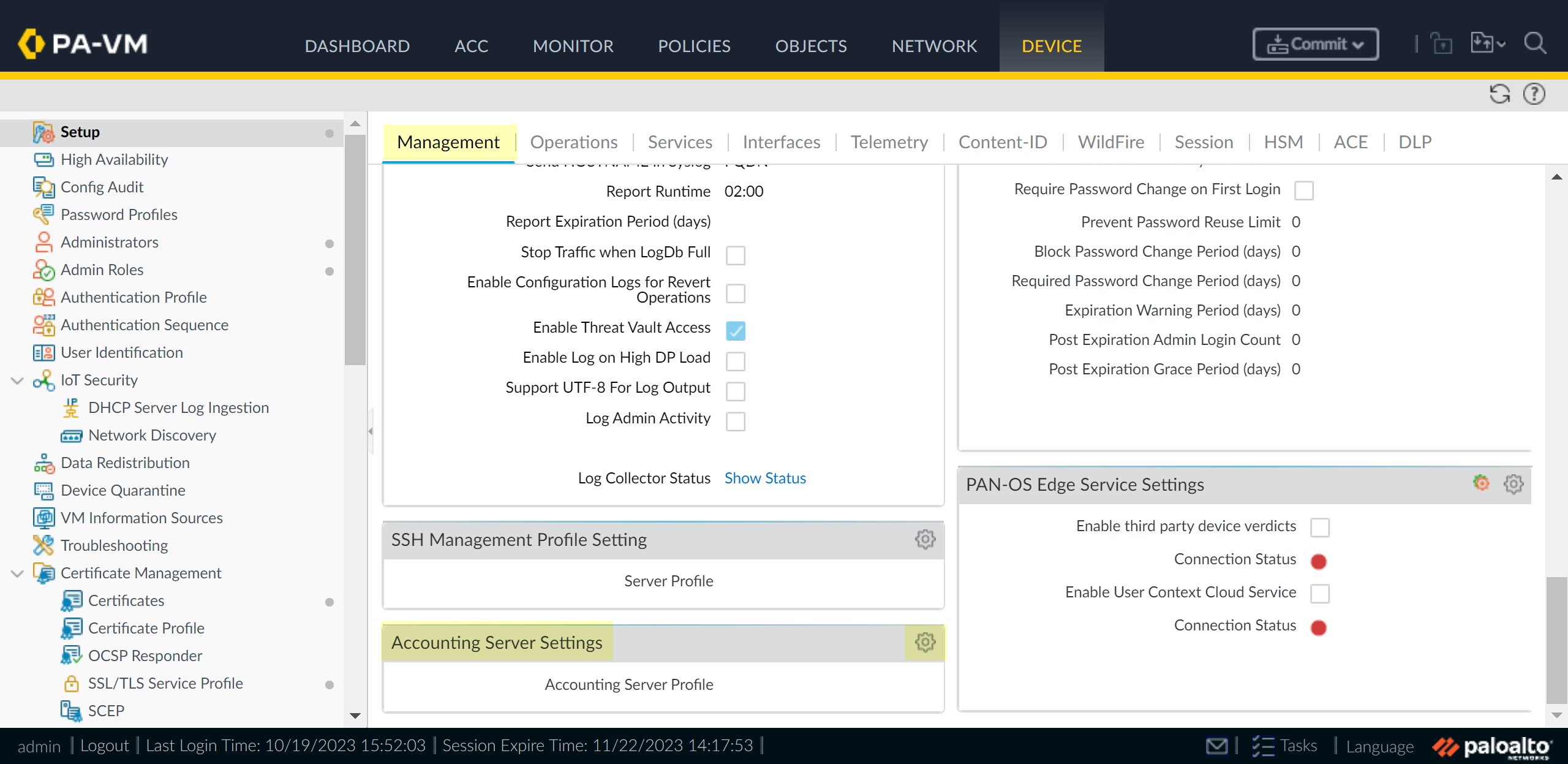
- For firewalls, select DeviceSetupManagement.
- For Panorama, select PanoramaSetupManagement.
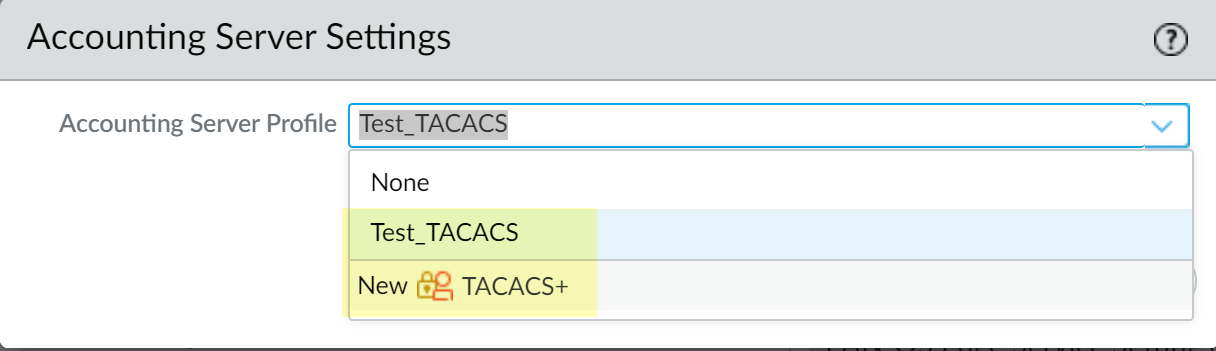
![]() Select the TACACS+ server profile or create a New TACACS+ server profile as the Accounting Server Profile and click OK.Palo Alto Networks recommends using port number 49 for accounting. This is the default port the firewall uses for accounting.
Select the TACACS+ server profile or create a New TACACS+ server profile as the Accounting Server Profile and click OK.Palo Alto Networks recommends using port number 49 for accounting. This is the default port the firewall uses for accounting.![]() Commit the changes.The TACACS+ accounting client attempts to connect to the first server in the TACACS+ server profile when the commit is successful. After it successfully connects, it logs the information in the TACACS+ accounting records.
Commit the changes.The TACACS+ accounting client attempts to connect to the first server in the TACACS+ server profile when the commit is successful. After it successfully connects, it logs the information in the TACACS+ accounting records.