Prisma Access
Explicit Proxy and GlobalProtect: Set It Up
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Explicit Proxy and GlobalProtect: Set It Up
Set up an explicit proxy with GlobalProtect or a third-party VPN.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
For your mobile users to connect securely, you can combine an explicit proxy with
GlobalProtect or a third-party VPN.
- Explicit Proxy and GlobalProtect
- Use GlobalProtect in split tunnel mode to provide secure access to private apps only.
- Use explicit proxy to secure public apps, including internet traffic and external SaaS applications.
- Explicit Proxy and third-party VPN
- Use a VPN client for access to data center and private applications and to secure access to private apps.
- Use an explicit proxy and a PAC file to secure access to public apps.
Before you decide which applications or traffic you should protect with an explicit proxy
and with either GlobalProtect or a third-party VPN, you should understand how
GlobalProtect and Prisma Access make their forwarding decisions based on the explicit
proxy and VPN configuration.
When a mobile user requests a private or internet-based resource or app, the request is
sent to the explicit proxy PAC file that is installed on the endpoint.
- Traffic that is specified in the PAC file as return "DIRECT"; bypasses explicit proxy processing. The DNS resolve (host) used with return "DIRECT"; allows specified IP pass explicit proxy processing.
- Traffic that is specified in the PAC file as return "PROXY sitename:8080"; is forwarded to an explicit proxy.
After the traffic is processed, it's then sent to GlobalProtect, direct to the internet,
or to explicit proxy, based on the PAC file and VPN processing.
The PAC file has the configuration to allow "internal-app.corp.com" to bypass explicit
proxy. When the mobile user requests "internal-app.corp.com" from their browser, the
browser evaluates the conditions in the PAC file. GlobalProtect notes that
"internal-app.corp.com" is listed in the Include Domain and sends it through the VPN
tunnel. GlobalProtect sends the request to the resource in "internal-app.corp.com" based
on the configuration options in GlobalProtect.
Explicit Proxy and GlobalProtect: Set It Up (Strata Cloud Manager)
Implement GlobalProtect Mobile Users with Explicit Proxy.
To implement GlobalProtect—Mobile Users with
Explicit Proxy, complete the following steps.
These configuration
steps make the following assumptions about your network environment;
if your network environment is different, the configuration might
be different:
- Mobile users are able to reach and resolve the GlobalProtect portal hostname, gateway FQDNs, Explicit Proxy URL, and PAC File URL.Here’s where to find this information:
- GlobalProtect Gateway FQDNs and Portal Hostname➡ Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructure and edit Infrastructure Settings.
- Explicit Proxy URL and PAC File URL➡ Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyInfrastructure and edit Infrastructure Settings.
- Mobile Users are able to resolve internal domains from GlobalProtect.
- Decide which applications you want to send to GlobalProtect and which applications you want to send to Explicit Proxy.The following steps direct private applications hosted at your data center to GlobalProtect and requests to internet and public SaaS applications to Explicit Proxy.Edit GlobalProtect portal settings.Go to GlobalProtectApp SettingsApp ConfigurationAdvanced Settings
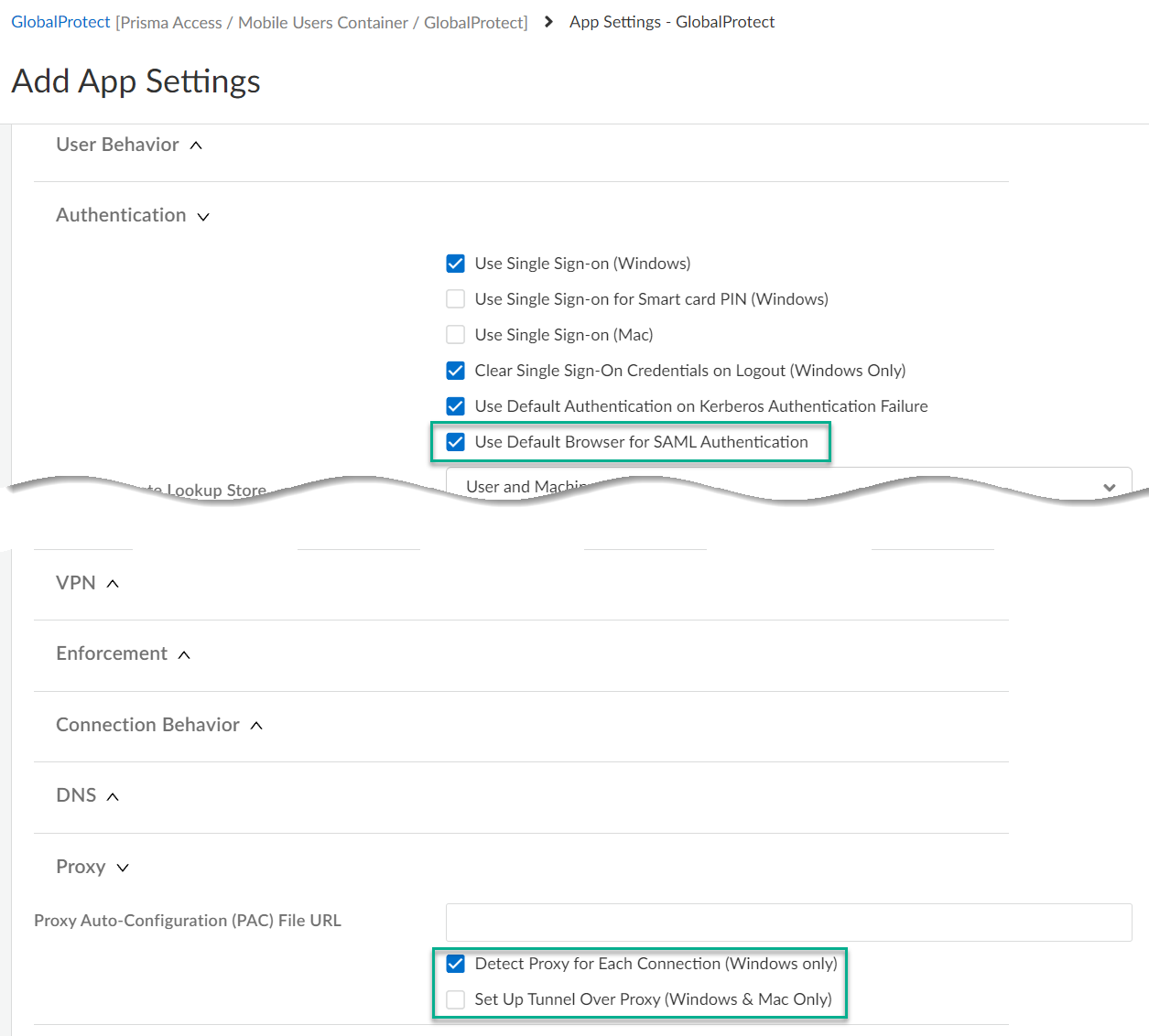
- In Proxy settings:
- Check Detect Proxy for Each Connection
- Clear Set Up Tunnel Over Proxy (Windows & Mac Only)
In Authentication settings:- Check Use Default Browser for SAML Authentication
![]() Create a split tunnel in GlobalProtect that allows you to direct the internal traffic to GlobalProtect.Go to GlobalProtectTunnel SettingsSplit Tunneling. Configure a split tunnel based on domain (FQDN), access routes, or applications.Configure the PAC file to exclude the domains you specified for the GlobalProtect split tunnel.To download the PAC file so you can edit it, go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyInfrastructureInfrastructure SettingsProxy Auto Configuration..The following example shows a PAC file with the URL that hosts private apps (internal-app.corp.com) bypassing the internal proxy. The parameters in the following PAC file are all example values:
Create a split tunnel in GlobalProtect that allows you to direct the internal traffic to GlobalProtect.Go to GlobalProtectTunnel SettingsSplit Tunneling. Configure a split tunnel based on domain (FQDN), access routes, or applications.Configure the PAC file to exclude the domains you specified for the GlobalProtect split tunnel.To download the PAC file so you can edit it, go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyInfrastructureInfrastructure SettingsProxy Auto Configuration..The following example shows a PAC file with the URL that hosts private apps (internal-app.corp.com) bypassing the internal proxy. The parameters in the following PAC file are all example values:- The portal hostname is splittunnel.gpcloudservice.com.
- The mobile user gateways are contained in the wildcard FQDN *examplegateways.gw.gpcloudservice.com.
- The PAC File URL is https://pacfileurl.pac.
- internal-app.corp.com is hosting the private apps that are being protected by Mobile Users—GlobalProtect.
- Okta is being used for SAML authentication.
- The Explicit Proxy URL is example.proxy.prismaacess.com.
function FindProxyForURL(url, host) { /* Bypass FTP */ if (url.substring(0,4) == "ftp:") return "DIRECT"; /* Bypass the Prisma Access Portal Hostname */ if (shExpMatch(host, "*.splittunnel.gpcloudservice.com")) return "DIRECT"; /* Bypass the Prisma Access Gateway */ if (shExpMatch(host, "*examplegateways.gw.gpcloudservice.com")) return "DIRECT"; /* Bypass the Prisma Access PAC File URL */ if (shExpMatch(host, "https://pacfileurl.pac")) return "DIRECT"; /* Bypass the URLs Being Sent to the GlobalProtect Portal */ if (shExpMatch(host, "*.internal-app.corp.com")) return "DIRECT"; /* Bypass ACS */ if (shExpMatch(host, "*.acs.prismaaccess.com")) return "DIRECT"; /* Forward to Prisma Access */ return "PROXY example.proxy.prismaaccess.com:8080"; }Explicit Proxy and GlobalProtect: Set It Up (Panorama)
Use this task to use Prisma Access Explicit Proxy with GlobalProtect.To implement GlobalProtect—Mobile Users with Explicit Proxy, complete the following steps.These configuration steps make the following assumptions about your network environment; if your network environment is different, the configuration might be different:- Mobile users are able to reach and resolve the GlobalProtect portal hostname, gateway FQDNs, Explicit Proxy URL, and PAC File URL.
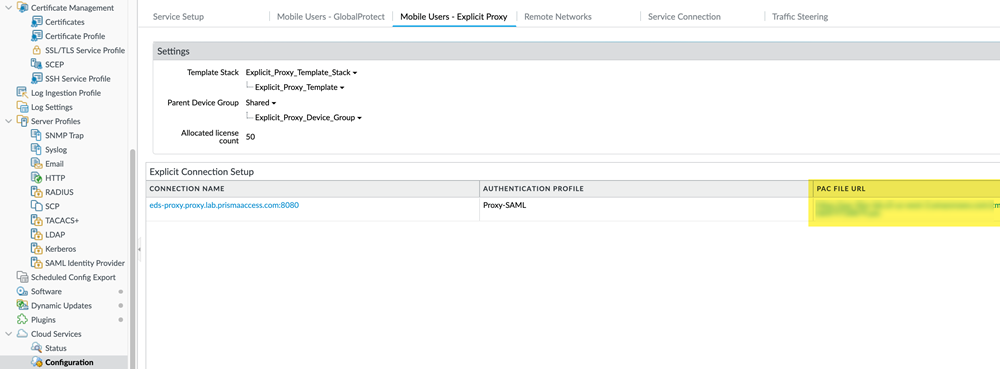
- To find the gateway FQDNs, select PanoramaCloud ServicesStatusNetwork DetailsMobile Users—GlobalProtectGateways.
- To find the PAC File URL, select PanoramaCloud ServicesConfigurationMobile Users—Explicit ProxyPAC File URL.
![]()
- Mobile Users are able to resolve internal domains from GlobalProtect.
- Plan your Mobile Users—Explicit Proxy deployment and your GlobalProtect deployment (either your Mobile Users—GlobalProtect or standalone GlobalProtect deployment).Decide which applications you want to send to GlobalProtect and which applications you want to send to Explicit Proxy.The following steps direct private applications hosted at your data center to GlobalProtect and requests to internet and public SaaS applications to Explicit Proxy.In the Panorama that manages Prisma Access, configure GlobalProtect portal settings.
- Select NetworkGlobalProtectPortals.Be sure that you are in the Mobile_User_Template from the Template drop-down.Select GlobalProtect_Portal to edit the Prisma Access portal configuration.Select the Agent tab and select the DEFAULT configuration or Add a new one.Select the App tab.Make the following app configuration changes:
- In Detect Proxy for Each Connection, select Yes.
- In Set Up Tunnel Over Proxy (Windows & Mac Only), select No.
- In Use Default Browser for SAML Authentication, select Yes.
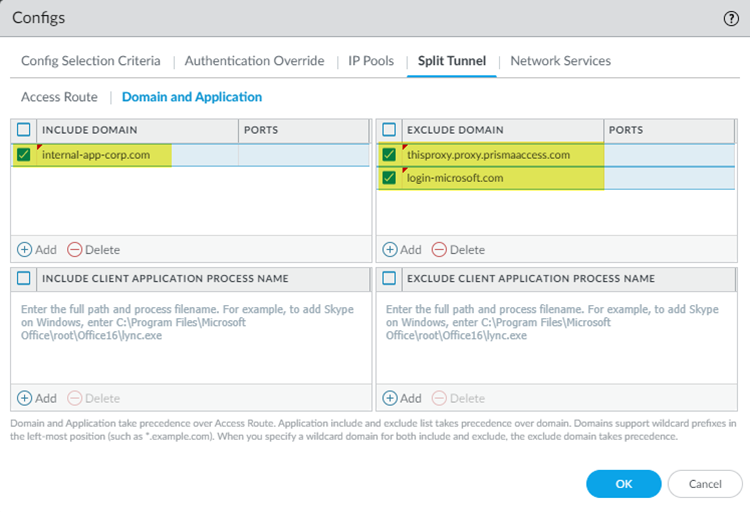
Create a split tunnel in GlobalProtect that allows you to direct the internal traffic to GlobalProtect.The following example uses a split tunnel to direct traffic based on domain (FQDN); you could also configure a split tunnel based on the access route of traffic.- While you are still in the GlobalProtect Agent configuration (NetworkGlobalProtectGatewaysGlobalProtect External Gateway), select AgentClient Settings.Select the DEFAULT configuration or Add a new one.Select Split TunnelDomain and Application.Add the Include Domain and, optionally, the Ports to use with the domain.This example uses internal-app.corp.com as the URL you use to host apps in your data center. You add this URL and the SAML authentication URL in the Exclude Domain.
![]() Click OK to save your changes.Commit and Push your changes.Configure the PAC file to exclude the domains you entered for split tunnel.The following example shows a PAC file with the URL that hosts private apps (internal-app.corp.com) bypassing the internal proxy. The parameters in the following PAC file are all example values:
Click OK to save your changes.Commit and Push your changes.Configure the PAC file to exclude the domains you entered for split tunnel.The following example shows a PAC file with the URL that hosts private apps (internal-app.corp.com) bypassing the internal proxy. The parameters in the following PAC file are all example values:- The portal hostname is splittunnel.gpcloudservice.com.
- The mobile user gateways (PanoramaCloud ServicesStatusNetwork DetailsMobile Users—GlobalProtectGateways) are contained in the wildcard FQDN *examplegateways.gw.gpcloudservice.com.
- The PAC File URL (PanoramaCloud ServicesConfigurationMobile Users—Explicit ProxyPAC File URL) is https://pacfileurl.pac.
- internal-app.corp.com is hosting the private apps that are being protected by Mobile Users—GlobalProtect.
- Okta is being used for SAML authentication.
- The Explict Proxy URL is example.proxy.prismaacess.com.
function FindProxyForURL(url, host) { /* Bypass FTP */ if (url.substring(0,4) == "ftp:") return "DIRECT"; /* Bypass the Prisma Access Portal Hostname */ if (shExpMatch(host, "*.splittunnel.gpcloudservice.com")) return "DIRECT"; /* Bypass the Prisma Access Gateway */ if (shExpMatch(host, "*examplegateways.gw.gpcloudservice.com")) return "DIRECT"; /* Bypass the Prisma Access PAC File URL */ if (shExpMatch(host, "https://pacfileurl.pac")) return "DIRECT"; /* Bypass the URLs Being Sent to the GlobalProtect Portal */ if (shExpMatch(host, "*.internal-app.corp.com")) return "DIRECT"; /* Bypass ACS */ if (shExpMatch(host, "*.acs.prismaaccess.com")) return "DIRECT"; /* Forward to Prisma Access */ return "PROXY example.proxy.prismaaccess.com:8080"; }