Download PDF
Prisma Access
Changes to Default Behavior for Prisma Access 5.2, 5.2.1, and 5.2.2
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Changes to Default Behavior for Prisma Access 5.2, 5.2.1, and 5.2.2
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The following sections detail the changes in default behavior for Prisma Access
version 5.2, version 5.2.1, and version 5.2.2.
Changes to Default Behavior for Prisma Access 5.2.2
The following table details the changes in default behavior for Prisma Access version 5.2.2.
| Component | Change |
|---|---|
| South Korea Mobile Users—GlobalProtect Location Group Remapping |
Before the Prisma Access 5.2.2 infrastructure upgrade,
the Location Group for the
South Korea location is mapped to a group that also contains
Japan South and Japan Central.
After the Prisma Access 5.2.2 infrastructure upgrade,
the South Korea location is mapped to its own location group.
If you have IP address pools configured for the Japan South,
Japan Central, and South Korea location group, Prisma Access uses IP addresses from the Worldwide IP
address pool instead of the location group in the following
cases:
To use IP pools for the remapped South Korea location group, add
a new IP pool for the South Korea location group after the
Prisma Access 5.2.2 infrastructure upgrade.
|
Changes to Default Behavior for Prisma Access 5.2.1
The following table details the changes in default behavior for Prisma Access version 5.2.1.
| Component | Change |
|---|---|
| IP Optimization Enabled for New Prisma Access Deployments | To enable faster onboarding of Prisma Access tenants and
simplify IP address allow listing, new Prisma Access
deployments have IP Optimization
enabled. IP Optimization deployments
do not support IPv6 for access to
public (external) apps; private app access is supported. To
enable IPv6 for your new Prisma Access deployment,
reach out to your Palo Alto Networks account team, who will open
a TAC case to accommodate the request. Be sure that all
users are running a GlobalProtect app version of 6.1.4 and
later, 6.2.3 and later, or 6.3.0 and later before setting up a
new Prisma Access deployment. New FedRAMP deployments do not have IP
Optimization enabled. |
| Default Mobile Users—GlobalProtect IP Address Pool Changed for New Prisma Access (Managed by Strata Cloud Manager) Deployments |
New Prisma Access (Managed by Strata Cloud Manager) Mobile
Users—GlobalProtect deployments has a new default IP address
pool: 100.92.0.0/16. This is a change from previous deployments
that used a default IP address pool of 100.127.0.0/16. You can
use this RFC6598 pool for the majority of use cases, including
for private app access for mobile users. If you require more IP
addresses, you can add them in the Prisma Access UI.
|
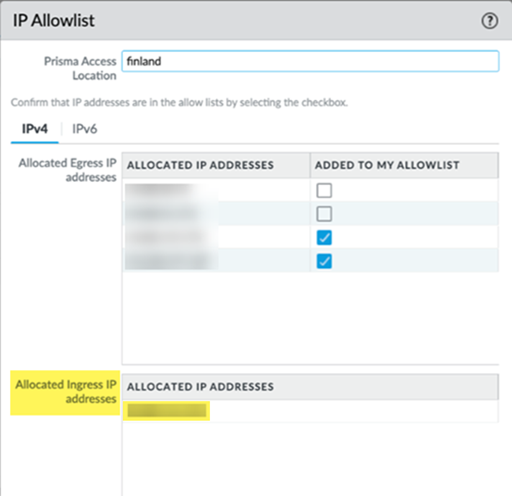
| IP Address Consolidation for Deployments that Have Migrated to IP Optimization |
If you have an existing Prisma Access that has had one or more
regions migrated to IP Optimization and
are using Prisma Access Allow
listing, some IP addresses that you have allow listed
have moved from the Allocated Egress IP
addresses area to the Allocated
Ingress IP addresses area in the Prisma Access UI. This change is a result of IP address
consolidation as a part of the Prisma Access 5.2.1
infrastructure upgrade. Your networks can still reach these IP
addresses and you no longer have to allow list them.
|
Changes to Default Behavior for Prisma Access 5.2
| Component | Change |
|---|---|
| Upgrade Considerations for the PAN-OS 10.2.10 Dataplane | If you choose to have Palo Alto Networks upgrade your dataplane to
PAN-OS 10.2.10 to support a Prisma Access 5.2 Preferred
feature, make sure that you're aware of the following 10.2-specific
changes and upgrade considerations before you schedule the upgrade:
|
| Upgrade Considerations for the PAN-OS 11.2.3 Dataplane | If you choose to have Palo Alto Networks upgrade your dataplane to
PAN-OS 11.2.3 to support a Prisma Access 5.2 Innovation
feature, make sure that you're aware of the following 11.2-specific
changes and upgrade considerations before you schedule the upgrade:
|
| Web Interface Changes in Prisma Access 5.1 | Some Prisma Access (Managed by Strata Cloud Manager) web interface changes were made in Prisma Access 5.1 to support a maximum of 25,000 remote networks. See 25,000 Remote Network and 50,000 IKE Gateway Support for details. |
