Prisma Access
Integrate Prisma Access with Cisco Meraki SD-WAN (Manual Integration)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
5.2 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
-
-
- Allocate Licenses for Prisma Access (Managed by Strata Cloud Manager)
- Plan Service Connections for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Add Additional Locations for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Enable Available Add-ons for Prisma Access (Managed by Strata Cloud Manager)
- Search for Subscription Details
- Share a License for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Increase Subscription Allocation Quantity
-
- Activate a License for Prisma Access (Managed by Strata Cloud Manager) and Prisma SD-WAN Bundle
- Activate and Edit a License for SASE 5G Through Common Services
-
- Prisma Access Onboarding Workflow
-
4.0 & Later
- 4.0 & Later
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
- Prisma Access China
-
- Set Up Prisma Access
- Configure the Prisma Access Service Infrastructure
- Remote Networks: IPSec Termination Nodes and Service IP Addresses
- Remote Networks: IP Address Changes Related To Bandwidth Allocation
- Remote Networks: Service IP Address and Egress IP Address Allocation
- API Examples for Retrieving Prisma Access IP Addresses
- Get Notifications When Prisma Access IP Addresses Change
- Prisma Access Zones
- DNS for Prisma Access
- High Availability for Prisma Access
-
- Enable ZTNA Connector
- Delete Connector IP Blocks
- Set Up Auto Discovery of Applications Using Cloud Identity Engine
- Private AWS Application Target Discovery
- Security Policy for Apps Enabled with ZTNA Connector
- Monitor ZTNA Connector
- View ZTNA Connector Logs
- Preserve User-ID Mapping for ZTNA Connector Connections with Source NAT
-
- Enable Dynamic Privilege Access for Prisma Access Through Common Services
- Authorize User Group Mapping in Cloud Identity Engine for Dynamic Privilege Access
- Enable the Access Agent
- Set Up the Agent Infrastructure for Dynamic Privilege Access
- Create a Snippet
- Create a Project
- Traffic Steering for Dynamic Privilege Access
- Push the Prisma Access Agent Configuration
- Download the Dynamic Privilege Access Enabled Prisma Access Agent Package
-
- Install the Prisma Access Agent
- Log in to the Dynamic Privilege Access Enabled Prisma Access Agent
- Change Preferences for the Dynamic Privilege Access Enabled Prisma Access Agent
- Connect the Dynamic Privilege Access Enabled Prisma Access Agent to a Different Location
- Switch to a Different Project
- Connect the Dynamic Privilege Access Enabled Prisma Access Agent to a Different Server
- Disable the Dynamic Privilege Access Enabled Prisma Access Agent
- Switch Between the Prisma Access Agent and GlobalProtect App
- View and Monitor Dynamic Privilege Access Users
- View and Monitor Dynamic Privilege Access Projects
- Automatic Tunnel Restoration in Dynamic Privilege Access Prisma Access Agents
- Manage Prisma SASE 5G
- App Acceleration in Prisma Access
-
-
- Planning Checklist for GlobalProtect on Prisma Access
- Set Up GlobalProtect Mobile Users
- GlobalProtect — Customize Tunnel Settings
- GlobalProtect — Customize App Settings
- Ticket Request to Disable GlobalProtect
- GlobalProtect Pre-Logon
- GlobalProtect — Clientless VPN
- Monitor GlobalProtect Mobile Users
- How the GlobalProtect App Selects Prisma Access Locations for Mobile Users
- Allow Listing GlobalProtect Mobile Users
-
- Explicit Proxy Configuration Guidelines
- GlobalProtect in Proxy Mode
- GlobalProtect in Tunnel and Proxy Mode
- Private IP Address Visibility and Enforcement for Agent Based Proxy Traffic
- SAML Authentication for Explicit Proxy
- Set Up Explicit Proxy
- Cloud Identity Engine Authentication for Explicit Proxy Deployments
- Proxy Mode on Remote Networks
- How Explicit Proxy Identifies Users
- Explicit Proxy Forwarding Profiles
- PAC File Guidelines
- Explicit Proxy Best Practices
- Monitor and Troubleshoot Explicit Proxy
- Block Settings for Explicit Proxy
- Use Special Objects to Restrict Explicit Proxy Internet Traffic to Specific IP Addresses
- Access Your Data Center Using Explicit Proxy
- App-Based Office 365 Integration with Explicit Proxy
- Chromebook with Prisma Access Explicit Proxy
- Configure Proxy Chaining with Blue Coat Proxy
- Configure Proxy Chaining on Prisma Access Explicit Proxy
- IP Address Optimization for Explicit Proxy Users- Proxy Deployments
- DNS Resolution for Mobile Users—Explicit Proxy Deployments
- View User to IP Address or User Groups Mappings
- Report Mobile User Site Access Issues
- Enable Mobile Users to Access Corporate Resources
-
-
- Planning Checklist for Remote Networks
- Allocate Remote Network Bandwidth
- Onboard a Remote Network
- Connect a Remote Network Site to Prisma Access
- Enable Routing for Your Remote Network
- Onboard Multiple Remote Networks
- Configure Remote Network and Service Connection Connected with a WAN Link
- Remote Networks—High Performance
- Integrate a Shared Desktop VDI with Prisma Access Using Terminal Server
-
- Multitenancy Configuration Overview
- Plan Your Multitenant Deployment
- Create an All-New Multitenant Deployment
- Enable Multitenancy and Migrate the First Tenant
- Add Tenants to Prisma Access
- Delete a Tenant
- Create a Tenant-Level Administrative User
- Sort Logs by Device Group ID in a Multitenant Deployment
-
- Add a New Compute Location for a Deployed Prisma Access Location
- How BGP Advertises Mobile User IP Address Pools for Service Connections and Remote Network Connections
- Proxy Support for Prisma Access and Strata Logging Service
- Block Incoming Connections from Specific Countries
- Prisma Access for No Default Route Networks
-
-
- Default Routes With Prisma Access Traffic Steering
- Traffic Steering in Prisma Access
- Traffic Steering Requirements
- Default Routes with Traffic Steering Example
- Default Routes with Traffic Steering Direct to Internet Example
- Default Routes with Traffic Steering and Dedicated Service Connection Example
- Prisma Access Traffic Steering Rule Guidelines
- Configure Zone Mapping and Security Policies for Traffic Steering Dedicated Connections
- Configure Traffic Steering in Prisma Access
- Preserve User-ID and Device-ID Mapping for Service Connections with Source NAT
-
- Prisma Access Internal Gateway
-
- Configure Privileged Remote Access Settings
- Set Up the Privileged Remote Access Portal
- Configure Applications for Privileged Remote Access
- Set Up Privileged Remote Access Profiles
- Define Permissions for Accessing Privileged Remote Access Apps
- Configure Split Tunneling for Privileged Remote Access Traffic
- Manage Privileged Remote Access Connections
- Use Privileged Remote Access
-
- Integrate Prisma Access With Other Palo Alto Networks Apps
- Integrate Third-Party Enterprise Browser with Explicit Proxy
- Integrate Third-Party NDRs with Prisma Access
- Juniper Mist Integration for SASE Health
-
-
- Connect your Mobile Users in Mainland China to Prisma Access Overview
- Configure Prisma Access for Mobile Users in China
- Configure Real-Name Registration and Create the VPCs in Alibaba Cloud
- Attach the CEN and Specify the Bandwidth
- Create Linux Instances in the Alibaba Cloud VPCs
- Configure the Router Instances
- Onboard the GlobalProtect Gateway and Configure the Prisma Access Portal
-
-
-
- INC_MU_APP_EXPERIENCE_UNREACHABLE_ ALL_PA_LOCATIONS
- INC_MU_APP_EXPERIENCE_UNREACHABLE_ PER_PA_LOCATION
- INC_RN_APP_EXPERIENCE_UNREACHABLE_ ALL_PA_LOCATIONS
- INC_RN_APP_EXPERIENCE_UNREACHABLE_ ONE_PA_LOCATION
- INC_CIE_AGENT_DISCONNECT
- INC_CIE_DIRECTORY_DISCONNECT
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_MU_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_MU_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_DNS_SERVER_UNREACHABLE_ PER_PA_LOCATION
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_RN_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_DNS_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_ECMP_TUNNEL_RTT_EXCEEDED_ BASELINE
- INC_RN_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SECONDARY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SITE_CAPACITY_PREDICTION
- INC_SC_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SITE_CAPACITY_PREDICTION
-
- INC_CERTIFICATE_EXPIRY
- INC_GP_CLIENT_VERSION_UNSUPPORTED
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_CAPACITY
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_THRESHOLD
- INC_PA_INFRA_DEGRADATION
- INC_PA_SERVICE_DEGRADATION_PA_LOCATION
- INC_PA_SERVICE_DEGRADATION_RN_ SITE_CONNECTIVITY
- INC_PA_SERVICE_DEGRADATION_SC_ CONNECTIVITY
- INC_RN_ECMP_BGP_DOWN
- INC_RN_ECMP_BGP_FLAP
- INC_RN_ECMP_PROXY_TUNNEL_DOWN
- INC_RN_ECMP_PROXY_TUNNEL_FLAP
- INC_RN_ECMP_TUNNEL_DOWN
- INC_RN_ECMP_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_BGP_FLAP
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_BGP_DOWN
- INC_RN_SECONDARY_WAN_BGP_FLAP
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_FLAP
- INC_RN_SITE_DOWN
- INC_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_RN_SPN_LONG_DURATION_CAPACITY_EXCEEDED _THRESHOLD
- INC_RN_SPN_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_SC_PRIMARY_WAN_BGP_DOWN
- INC_SC_PRIMARY_WAN_BGP_FLAP
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_PRIMARY_WAN_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_BGP_DOWN
- INC_SC_SECONDARY_WAN_BGP_FLAP
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_TUNNEL_FLAP
- INC_SC_SITE_DOWN
- INC_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_SC_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- INC_ZTNA_CONNECTOR_CPU_HIGH
- INC_ZTNA_CONNECTOR_MEMORY_HIGH
- INC_ZTNA_CONNECTOR_TUNNEL_DOWN
-
- AL_CIE_AGENT_DISCONNECT
- AL_CIE_DIRECTORY_DISCONNECT
- AL_MU_IP_POOL_CAPACITY
- AL_MU_IP_POOL_USAGE
- AL_RN_ECMP_BGP_DOWN
- AL_RN_ECMP_BGP_FLAP
- AL_RN_PRIMARY_WAN_BGP_DOWN
- AL_RN_PRIMARY_WAN_BGP_FLAP
- AL_RN_PRIMARY_WAN_TUNNEL_DOWN
- AL_RN_PRIMARY_WAN_TUNNEL_FLAP
- AL_RN_SECONDARY_WAN_BGP_DOWN
- AL_RN_SECONDARY_WAN_BGP_FLAP
- AL_RN_SECONDARY_WAN_TUNNEL_DOWN
- AL_RN_SECONDARY_WAN_TUNNEL_FLAP
- AL_RN_SITE_DOWN
- AL_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- AL_RN_SPN_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_PRIMARY_WAN_BGP_DOWN
- AL_SC_PRIMARY_WAN_BGP_FLAP
- AL_SC_PRIMARY_WAN_TUNNEL_DOWN
- AL_SC_PRIMARY_WAN_TUNNEL_FLAP
- AL_SC_SECONDARY_WAN_BGP_DOWN
- AL_SC_SECONDARY_WAN_BGP_FLAP
- AL_SC_SECONDARY_WAN_TUNNEL_DOWN
- AL_SC_SECONDARY_WAN_TUNNEL_FLAP
- AL_SC_SITE_DOWN
- AL_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_SITE_LONG_DURATION_EXCEEDED_CAPACITY
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- AL_ZTNA_CONNECTOR_CPU_HIGH
- AL_ZTNA_CONNECTOR_MEMORY_HIGH
- AL_ZTNA_CONNECTOR_TUNNEL_DOWN
- New Features in Incidents and Alerts
- Known Issues
Integrate Prisma Access with Cisco Meraki SD-WAN (Manual Integration)
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To secure a Meraki SD-WAN with Prisma Access (Managed by Strata Cloud Manager), complete the following
steps.
- Onboard a remote network to use with the Meraki SD-WAN in Cloud Managed Prisma Access.
- If you have not already, allocate bandwidth for the remote network.You allocate bandwidth by selecting bandwidth for the remote network’s compute location. Go to ManageService SetupRemote NetworksBandwidth Management and select an Assigned Bandwidth for the remote network’s compute location.
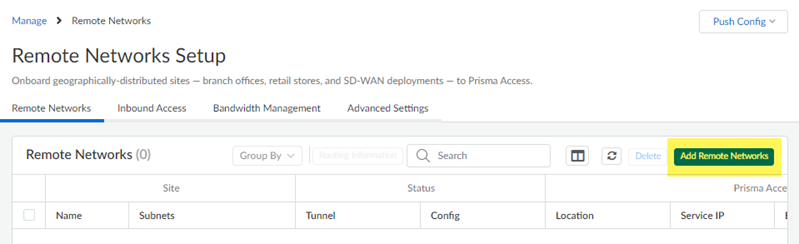
- Go to ManageService SetupRemote Networks and Add Remote Networks.

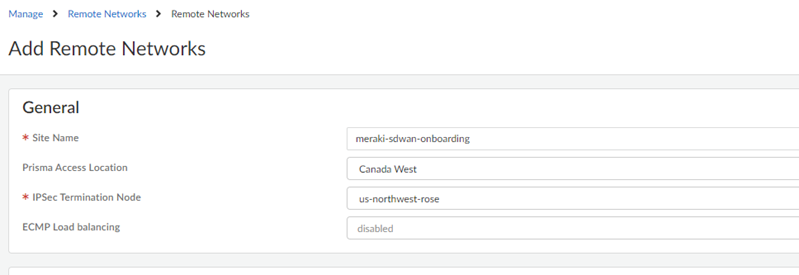
- Give the remote network a descriptive Site Name.
- Select the Prisma Access Location for the remote network.
- Select the IPSec Termination Node to use for the remote network.Don’t enable ECMP Load Balancing; BGP routing isn’t supported with Meraki integrations. The Meraki SD-WAN can’t share traffic between several different links and you can only have one operational tunnel to the Meraki SD-WAN. However, you can optionally use a secondary tunnel using another WAN as a standby.

- Set up the IPSec tunnel to use with the Meraki SD-WAN.
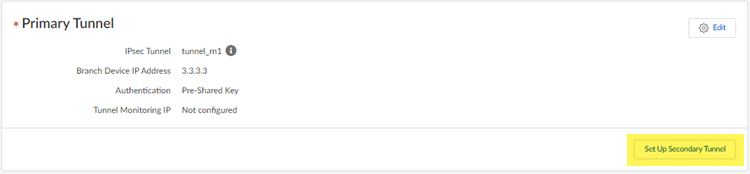
- Set Up the primary tunnel.

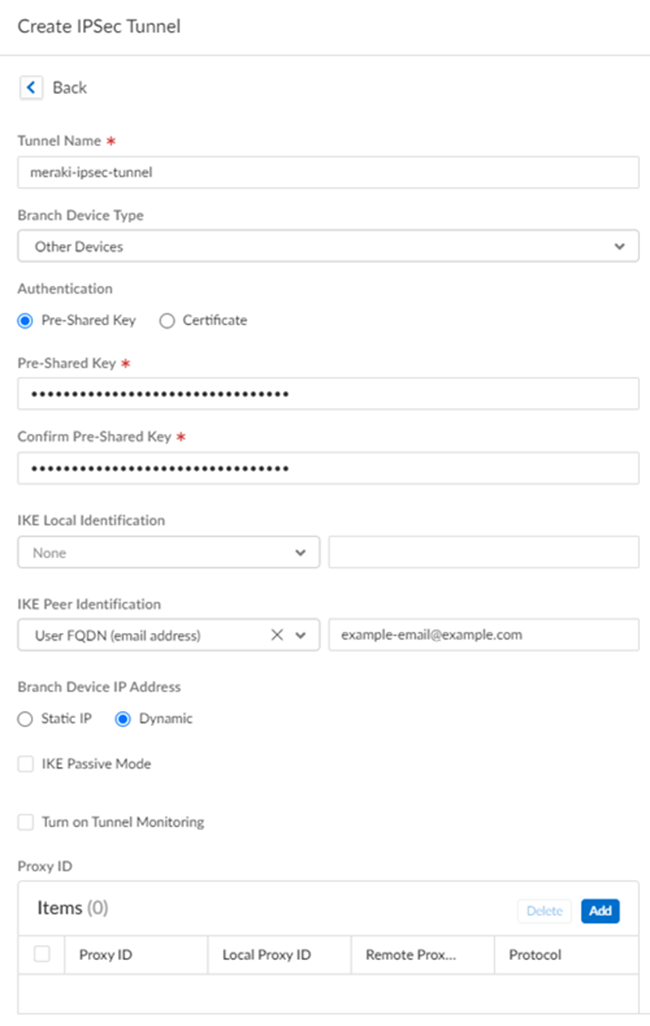
- Select an existing tunnel, or select Create New to create a new tunnel.

- Give the tunnel a descriptive Name.
- In the Branch Device Type, select Other Devices.
- Specify a Pre-Shared Key or a Certificate to use for authentication.This example uses a pre-shared key (PSK) for authentication.
- Specify an IKE Peer Identification method.If you select a Branch Device IP Address of Dynamic, you must select an IKE peer identification. This example has IKE Peer Identification set up and uses a method of User FQDN (email address). Be sure that you select the same email address on the Meraki SD-WAN side of the IPSec tunnel.
- Specify a Branch Device IP Address of either Static IP or Dynamic IP.Setting up an IKE Peer Identification is required if you use a dynamic IP address. If you select Static IP, enter a static IP address.
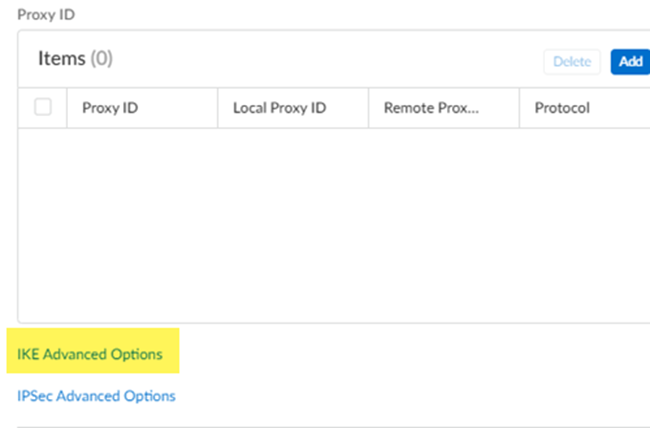
- Don’t enter Proxy ID information.Meraki creates a crypto map with routing and you don’t need to configure proxy IDs.

- Select IKE options for the remote network IPSec tunnel.
- Select IKE Advanced Options.

- Select an IKE Protocol Version.The IKE version depends on what the Meraki SD-WAN supports. Meraki SD-WAN devices with a firmware version of 15.12 or later support IKEv2 options. If you don’t know which version the Meraki device supports, select ikev2-preferred-mode; in this mode, Prisma Access selects the IKE version to use, with IKEv2 being preferred.
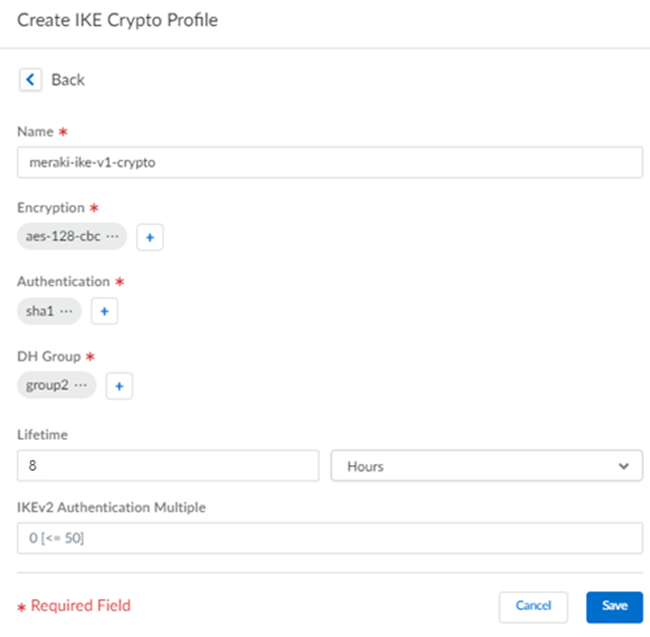
- (IKEv1 or IKEv2 Preferred Deployments Only) Select an existing IKEv1 Crypto Profile or specify Create New to create one.If you create a new profile, specify a descriptive Name for it.
- Specify the following IKEv1 options:
- Encryption—Specify the encryption algorithm used in the IKE SA negotiation. The Meraki SD-WAN device supports the following encryption types:
- aes-128-cbc
- aes-128-gcm
- aes-192-cbc
- aes-256-cbc
- aes-256-gcm
- 3DES
You can specify multiple encryption types in a single profile. - Authentication—Specify the authentication algorithm used in the IKE SA negotiation. The Meraki SD-WAN device supports the md5, sha1, or sha256 algorithm. You can specify multiple authentication types.
- DH Group—Specify the Diffie-Hellman (DH) groups used to generate symmetrical keys for IKE in the IKE SA negotiation. The Meraki SD-WAN device supports the group1, group2, group5, group14 groups. You can specify multiple DH group types.For the strongest security, select the group with the highest number. If you don’t want to renew the key that Prisma Access creates during IKE phase 1, select no-pfs (no perfect forward secrecy). If you select this option, Prisma Access reuses the current key for the IPSec SA negotiation.
- Lifetime—Specify the unit and amount of time for which the IKE Phase 1 key is valid (default is 8 hours).For IKEv1, the security association (SA) isn’t actively re-keyed before the key lifetime expires. The IKEv1 Phase 1 re-key triggers only when the SA expires. For IKEv2, the SA must be re-keyed before the key lifetime expires. If the SA isn’t re-keyed upon expiration, the SA must begin a new Phase 1 key.

- Save your changes.
- (IKEv2 or IKEv2 Preferred Deployments only) Select an existing IKEv2 Crypto Profile and select Create New to create one.If you create a new profile, specify a descriptive Name for it.
- Specify the following IKEv2 options:
- Encryption—Specify one or more of the following encryption algorithms:
- aes-128-cbc
- aes-128-gcm
- aes-192-cbc
- aes-256-cbc
- aes-256-gcm
- 3DES
You can specify multiple encryption algorithms in a single profile. - Authentication—Specify md5, sha1, or any combination of these authentication algorithms.
- DH Group—Specify group1, group2, group5, group14, or any combination of these DH group types.
- Lifetime—Enter the phase 1 lifetime in hours or seconds (default is 8 hours).
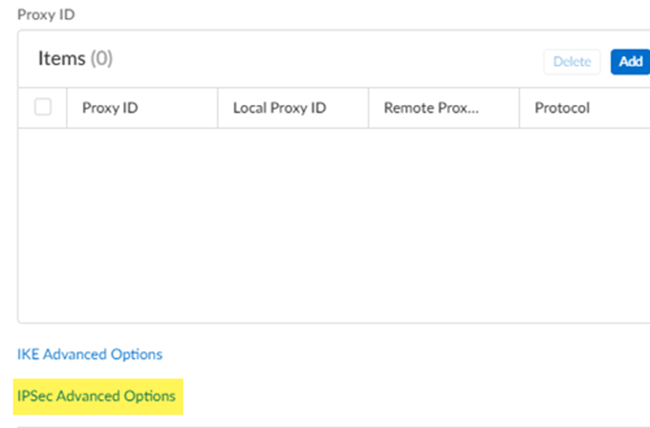
- Select IPSec advanced options for the remote network IPSec tunnel.
- Select IPSec Advanced Options.

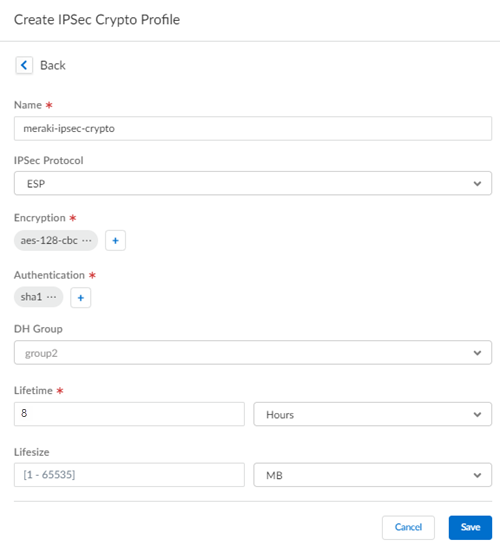
- Select an existing IPSec Crypto Profile and select Create New to create one.If you create a new profile, specify a descriptive Name for it.
- Specify the following IPSec crypto options:
- Encryption—Specify one or more or the following encryption algorithms:
- aes-128-cbc
- aes-128-gcm
- aes-192-cbc
- aes-256-cbc
- aes-256-gcm
- 3DES
- Authentication—Specify md5, sha1, sha256, or any combination of these authentication algorithms.
- DH Group—Specify group1, group2, group5, group14, or any combination of these DH group types.
- Lifetime—Enter the phase 1 lifetime in hours or seconds (default is 8 hours).

- Save your changes.
- (Optional) If you want to use a standby (secondary) tunnel, go to ManageService SetupRemote Networks, select Set Up Secondary Tunnel, and repeat step2through step4for the secondary tunnel.When both tunnels are up, the primary tunnel takes priority over the secondary tunnel. If the primary tunnel for a remote network site goes down, the remote network falls back to the secondary tunnel until the primary tunnel comes back up. It can take at least 30-40 seconds before the secondary tunnel comes up after a failover.

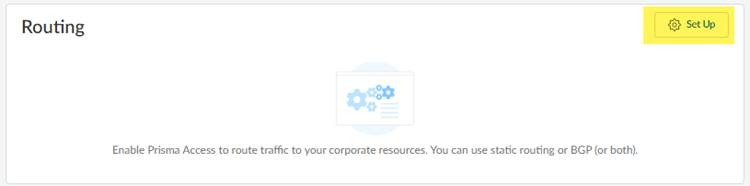
- Configure routing for the remote network.
- Return to ManageService SetupRemote Networks and Set Up routing for the remote network.

- Add the IP subnets or IP addresses that you want to secure at the branch. If you make any changes to the IP subnets on your branch, you must manually update the static routes.Dynamic (BGP) routing isn’t supported for use with Meraki SD-WAN devices.

- Save your changes.
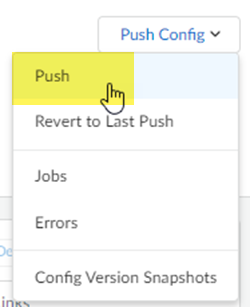
- Push your configuration changes.
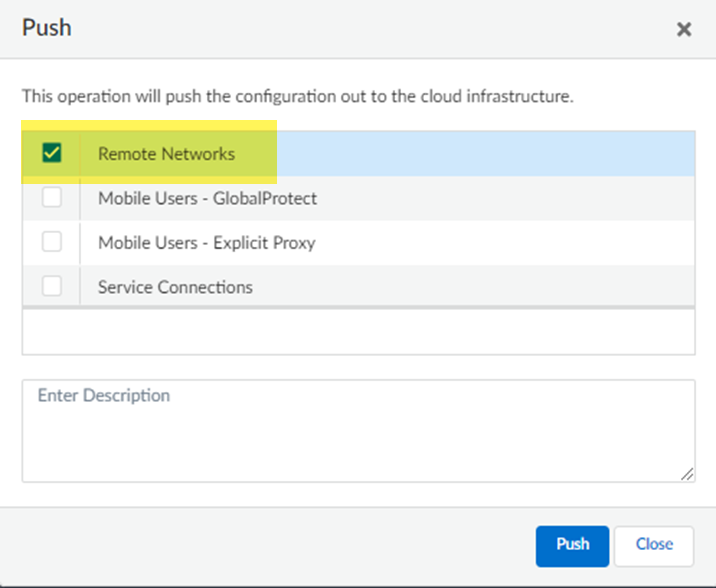
- Return to ManageService SetupRemote Networks and select Push ConfigPush.

- Select Remote Networks.

- Push your changes.
- Find the IP address used on the Prisma Access side of the IPSec tunnel.
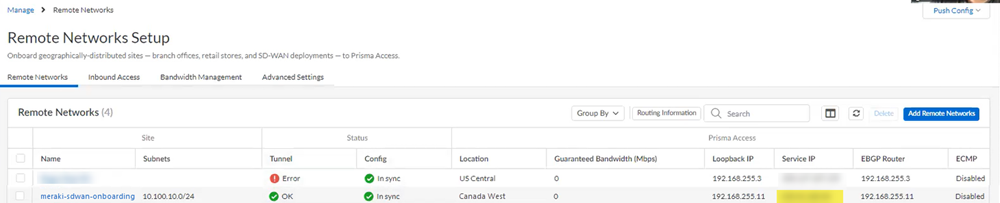
- Go to ManageService SetupRemote Networks and make a note of the Service IP address.You use this IP address as the peer address when you set up the IPSec tunnel on the Meraki SD-WAN.

- Set up the Meraki SD-WAN device.
- From the Meraki SD-WAN device, Go to Security & SD-WANConfigure> Site-to-site VPN.
- Find the Organization-wide settings area.
- Under Non-Meraki VPN peers, Add a peer.
- Create a peer for Prisma Access.
- Specify the IKE Version and make sure that it matches the version you specified in Prisma Access.
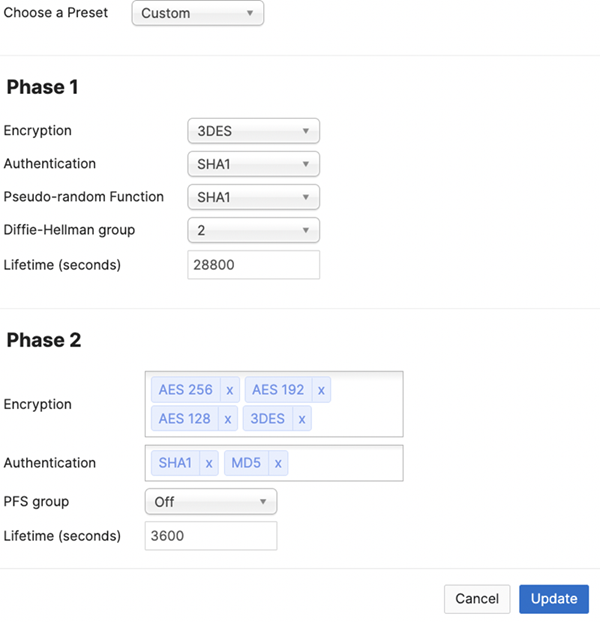
- (Optional) If required, select Custom in the IPSec Policies area and make sure that the Phase 1 and Phase 2 IPSec tunnel settings match with the IPSec tunnel settings you entered in Prisma Access.

- Enter the Service IP address from Prisma Access as the Public IP / Hostname.
- (Optional) if you’re used an IKE Peer Identification of User FQDN (email address) in Prisma Access, enter the same email address as the Local ID.If you’re using a static IP address in the branch, this field will be blank.
- Enter the Private subnets that will be sent through the IPSec tunnel.Palo Alto Networks recommends that you enter an all-zeros (default) route.
- (Optional) If you’re using PSKs for the IPSec tunnel, enter a Preshared secret that matches the Pre-Shared Key you entered in Prisma Access.
- Verify that the IPSec tunnel is up and running.
- Check the IPSec tunnel status from Prisma Access.
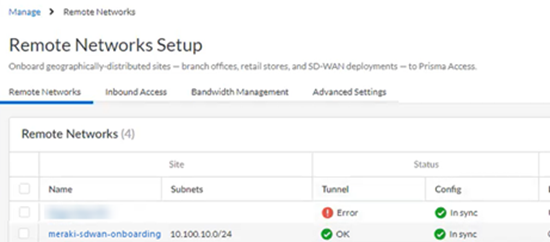
- Go to ManageService SetupRemote Networks and check the Status of the tunnel.It might take some time (10 minutes or longer) for the IPSec tunnel to come up, especially if you’re using the cloud version of the Meraki web interface to configure Meraki.

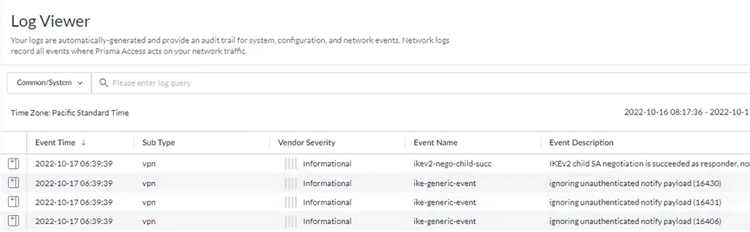
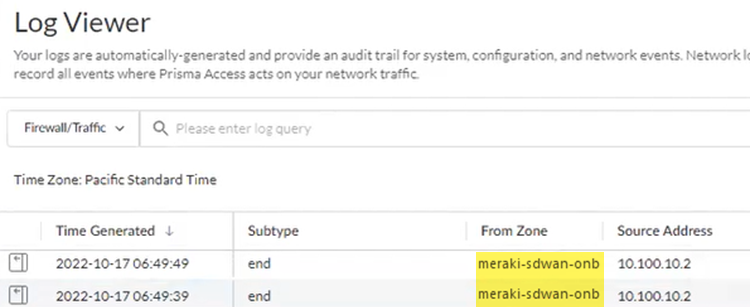
- Go to ActivityLog Viewer and check the Common/System logs for IPSec- and IKE-related messages.The following message ignoring unauthenticated notify payload indicates that the route has not been added in the crypto map on the other side of the IPSec tunnel after the IPSec negotiation has already occurred.

- Check the Firewall/Traffic logs and view the messages that are coming from the zone that has the same name as the remote network.In the logs, the remote network name is used as the source zone.

- From the Meraki web interface, check the status of the non-Meraki VPN and view its Status.