Prisma Access
Prisma Access Internal Gateway (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Prisma Access Internal Gateway (Strata Cloud Manager)
Learn how to set up the Prisma Access internal gateway and its
requirements.
Complete the following steps to set up the Prisma Access internal gateway.
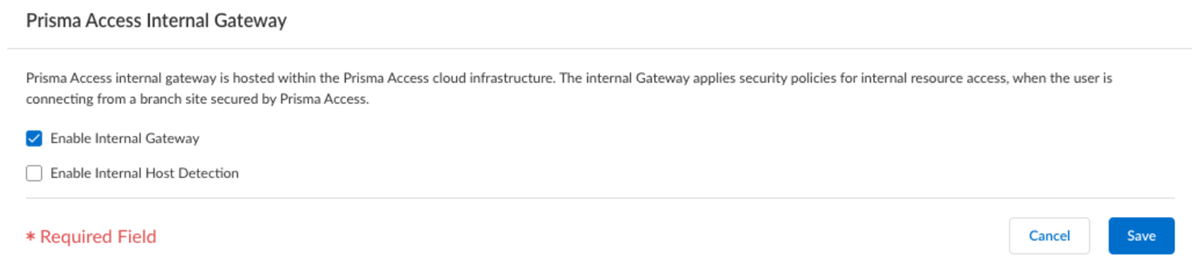
- In Strata Cloud Manager, set up GlobalProtect, add app settings, and onboard remote networks.Notice that there are no internal host detection and internal gateway configurations at present.Make a note of the Remote Networks DNS IP Address from ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma Access Infrastructure.Make a note of the Gateway FQDNs from ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructureInfrastructure SettingsGateway FQDNs.Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote NetworksAdvanced Settings.Edit the settings of Prisma Access Internal Gateway to enable the internal gateway and Save the changes.(Optional) Enable Internal Host Detection for IPv4 if you don't want to use your own DNS server. You can enable the internal host detection only after you select Enable Internal Gateway.
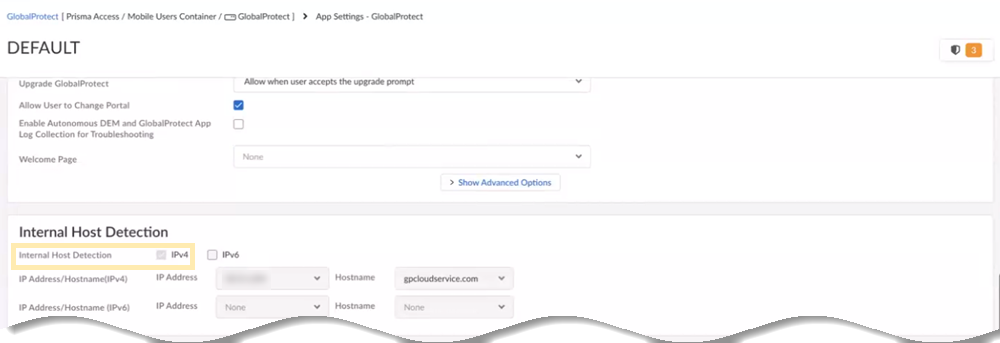
![]() When you enable the internal gateway, the remote network instances act as internal gateways. When you enable the internal host detection, Prisma Access creates PTR records on the remote network DNS proxy servers for the internal host detection process.Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectGlobalProtect App.Select an app setting and view the internal host detection details and internal gateway details.When you enable the internal gateway and internal host detection in step 5, Prisma Access enables IPv4 internal host detection and internal gateway here as well. Prisma Access populates the Remote Networks DNS IP Address value, from step 2, as the IP address.
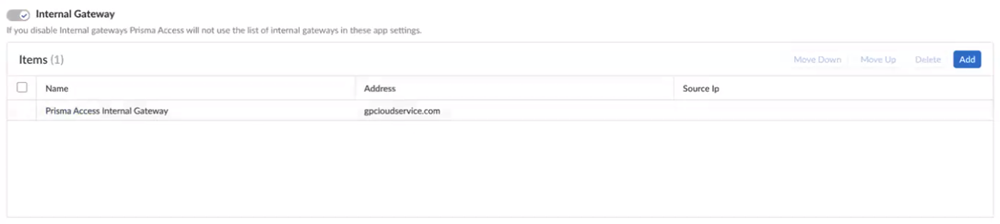
When you enable the internal gateway, the remote network instances act as internal gateways. When you enable the internal host detection, Prisma Access creates PTR records on the remote network DNS proxy servers for the internal host detection process.Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectGlobalProtect App.Select an app setting and view the internal host detection details and internal gateway details.When you enable the internal gateway and internal host detection in step 5, Prisma Access enables IPv4 internal host detection and internal gateway here as well. Prisma Access populates the Remote Networks DNS IP Address value, from step 2, as the IP address.![]() IPv6 internal host detection on Prisma Access DNS proxies isn't supported.You can't remove this Prisma Access Internal Gateway entry. However, you can add your self-deployed internal gateways. You can deploy your own DNS servers in the internal network for internal host detection, but ensure to add PTR records so that the internal host detection is possible. Prisma Access appends the Gateway FQDNs value, from step 3, to the address.
IPv6 internal host detection on Prisma Access DNS proxies isn't supported.You can't remove this Prisma Access Internal Gateway entry. However, you can add your self-deployed internal gateways. You can deploy your own DNS servers in the internal network for internal host detection, but ensure to add PTR records so that the internal host detection is possible. Prisma Access appends the Gateway FQDNs value, from step 3, to the address.![]() You can view the DNS proxy server IP address details by selecting ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma Access Infrastructure.If you enable Internal Host Detection, verify that the DNS resolution is working, perform a reverse DNS lookup from your internal network to DNS proxy server IP address, and ensure it returns an FQDN starting with any-igw.Push the changes to mobile users and remote networks at the same time.Log in to the endpoint.When you connect to GlobalProtect, first you authenticate with the GlobalProtect portal. The internal host detection triggers GlobalProtect to connect to the internal gateway. Then, as the GlobalProtect app continues to operate in the nontunnel mode, the second authentication appears and submits the host information to the internal gateway on remote networks.
You can view the DNS proxy server IP address details by selecting ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma Access Infrastructure.If you enable Internal Host Detection, verify that the DNS resolution is working, perform a reverse DNS lookup from your internal network to DNS proxy server IP address, and ensure it returns an FQDN starting with any-igw.Push the changes to mobile users and remote networks at the same time.Log in to the endpoint.When you connect to GlobalProtect, first you authenticate with the GlobalProtect portal. The internal host detection triggers GlobalProtect to connect to the internal gateway. Then, as the GlobalProtect app continues to operate in the nontunnel mode, the second authentication appears and submits the host information to the internal gateway on remote networks.